Twitter is one of the most influential social media platform, so it is no secret that many people want to hack Twitter. What do they want to achieve, and how can they pull this off? In this “Hack Twitter” guide we will see an answer to all these questions, as well as how to protect yourself.
Of course, this is a guide where we talk about how people hack Twitter. It will be somewhat technical, but something anyone should be able to follow. Before we start, however, let’s give you a quick disclaimer. With this guide we are not meaning to teach you to hack Twitter so that you can use it for ill reasons. The purpose of this guide is to show you what hackers do and how you can protect yourself. We do not endorse any illegal or dubious behavior: you are responsible of your own actions.
Hack Twitter to Steal an Account
This is probably the most wanted Twitter Hack, and the one hackers try so badly. On Twitter you find highly influential people, that often use Twitter as their main communication channel, such as Elon Musk. Because of this, hackers want to try and steal these influential accounts and use them for whatever reason.
No matter how big or small your Twitter account is. Someone may be attempting to hack it. How would they do it?
Hack Twitter with Phishing
The simplest strategy most hackers follow is called phishing. The idea is simple: Twitter servers are so strong and protected by highly capable engineers that the individual hacker stands no chance of breaching into them. However, users tend to be vulnerable, so the way hackers try to steal an account is to attack the user directly.
Here, we don’t mean attacking their computer or smartphone. We mean attacking the user as a person, and having him or her disclose the password voluntarily. Basically, the hacker goes to the user and asks “Hey, can you give me your password?” and the user will say “Yes of course, here it is!”. This is an extreme dramatization, but it explains what phishing is about.
The hackers is smart enough that he knows he can’t just “ask” the user for the password. Instead, he pretend to be Twitter, for example asking for a fake password reset. This is done via phishing emails, which are the most common method to hack Twitter. How can phishing emails be pulled off? That is actually easy to do, so let’s see that so that you will know how to protect yourself.
Creating a Phishing Email
Creating a phishing email to hack Twitter is not that hard. All the hacker needs to do is have an original email from Twitter and edit it. To get such an email, all the hacker needs to do is do a password reset for his own account. If he doesn’t have one, he can just create a new account and then immediately ask for the password reset.
As a first step to hack a twitter account, you would go to the login page and click on “Forgot password?”.
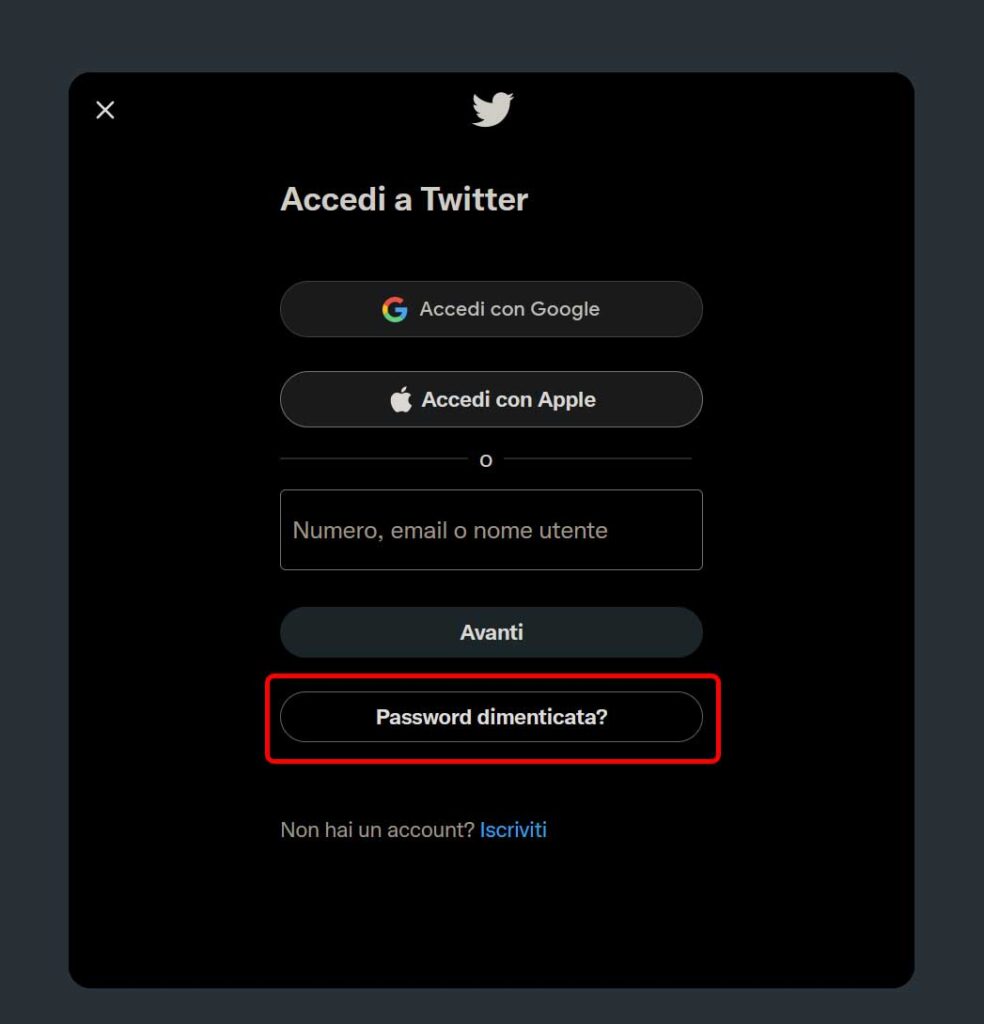
Then, you would have to add your own email address. This is not the email address of the victim the hacker is targeting, it is the hacker’s email address. The hacker does this because he needs to receive the original email from Twitter to modify it and make it malicious.
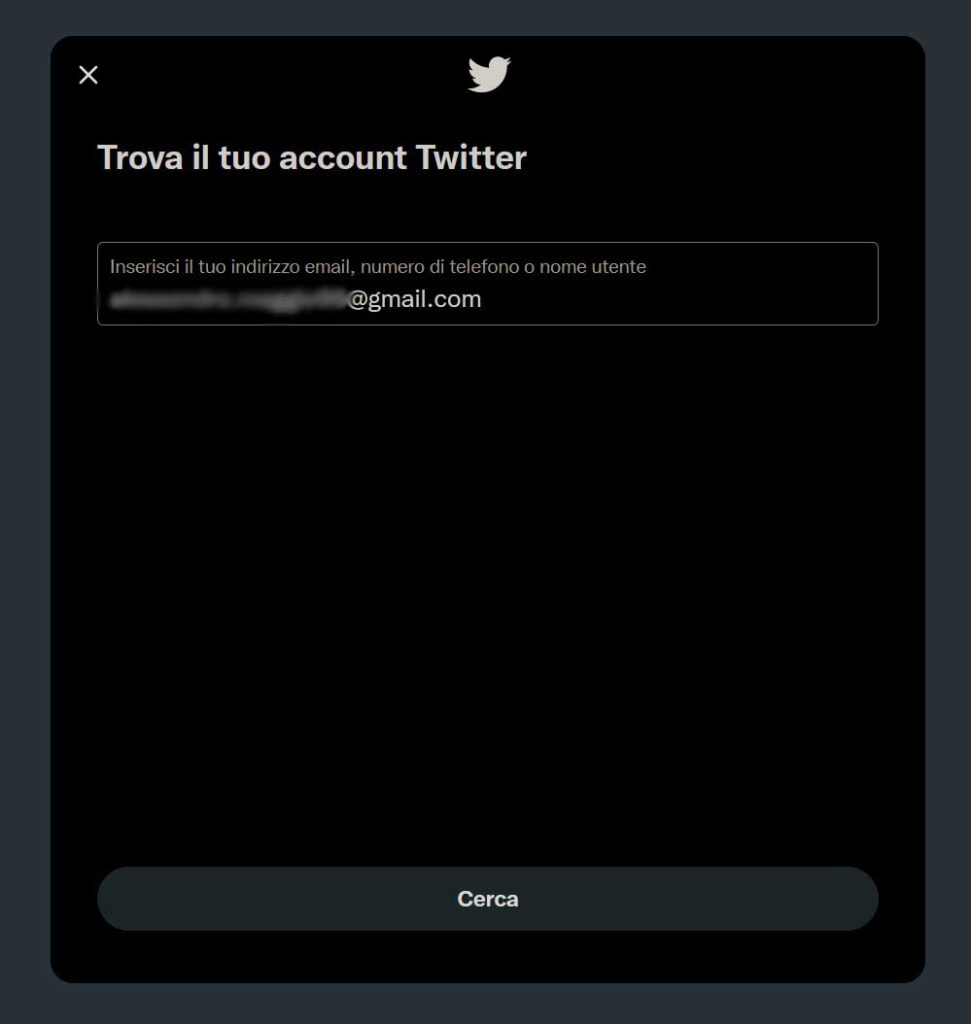
As a next step, Twitter often asks to write the username associated with the email address. Do it and proceed.
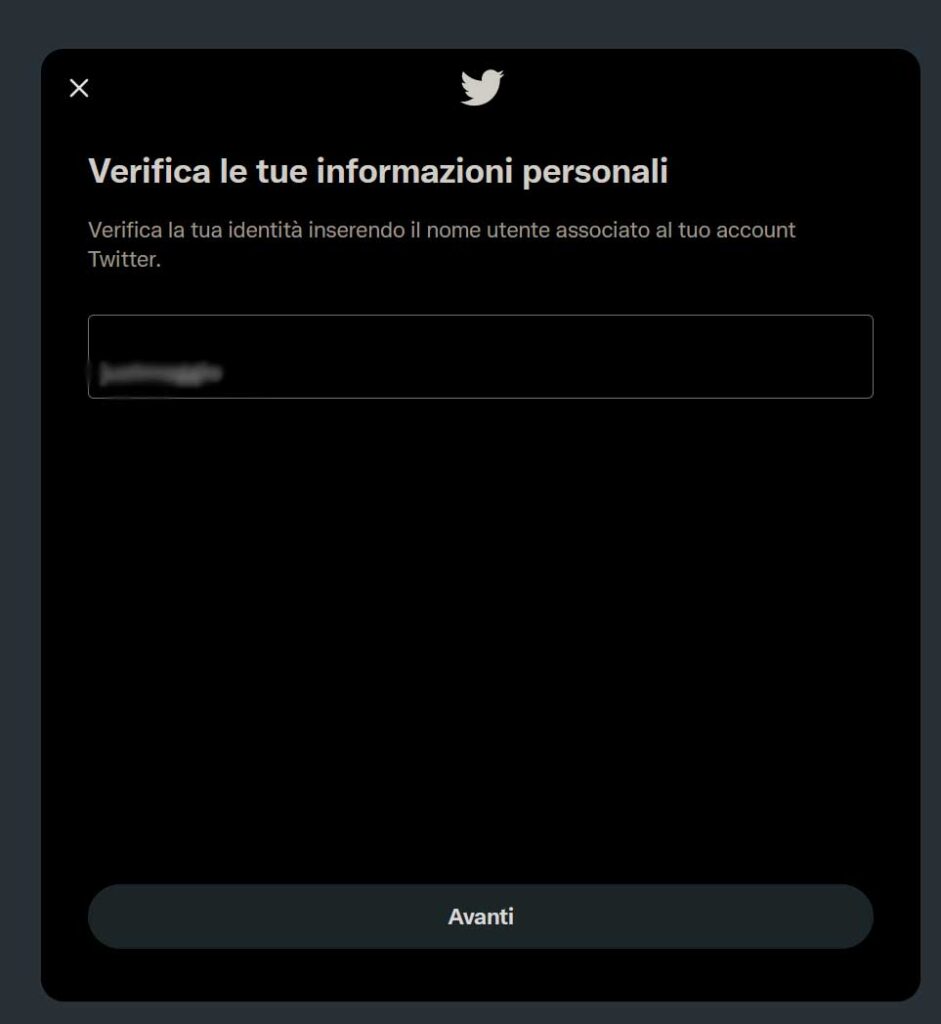
Then, it may also ask for phone number, depending on some factors such as how “big” the account is and how often it has been used recently.
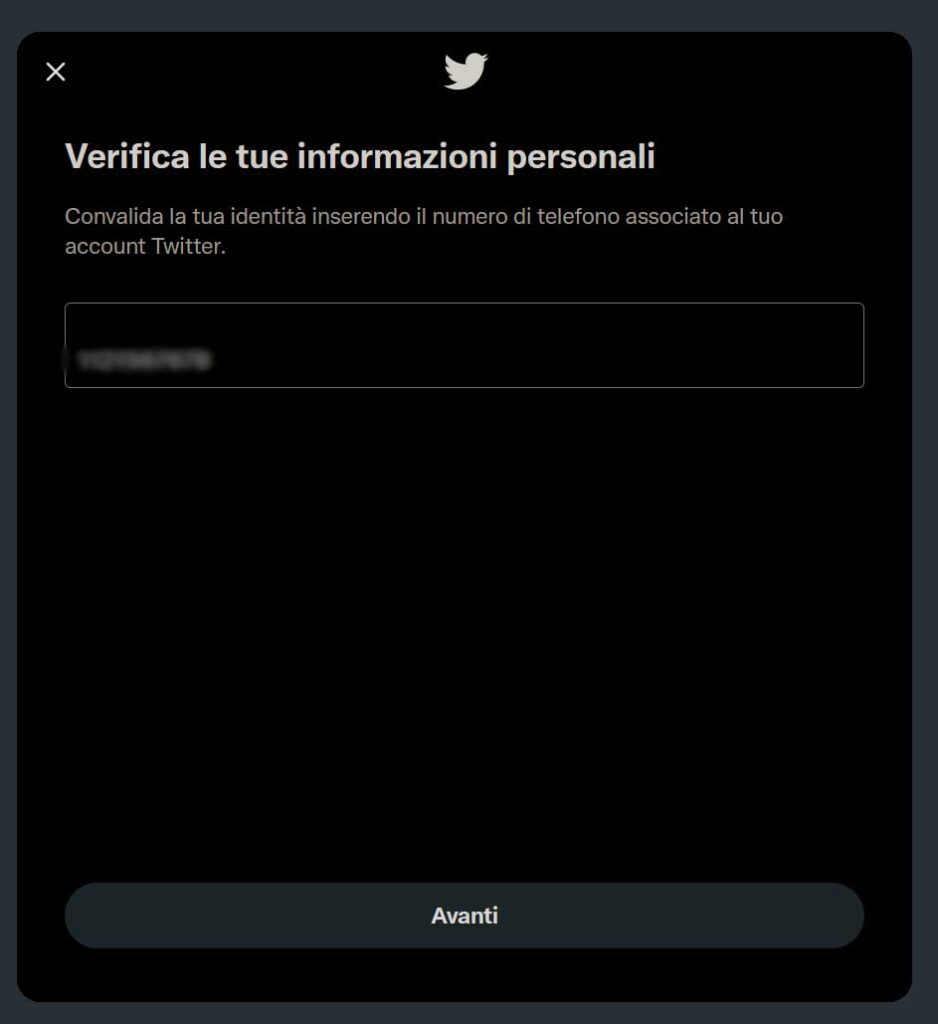
Then, when asked how you prefer to reset the password, you should pick the first option: send code via email.
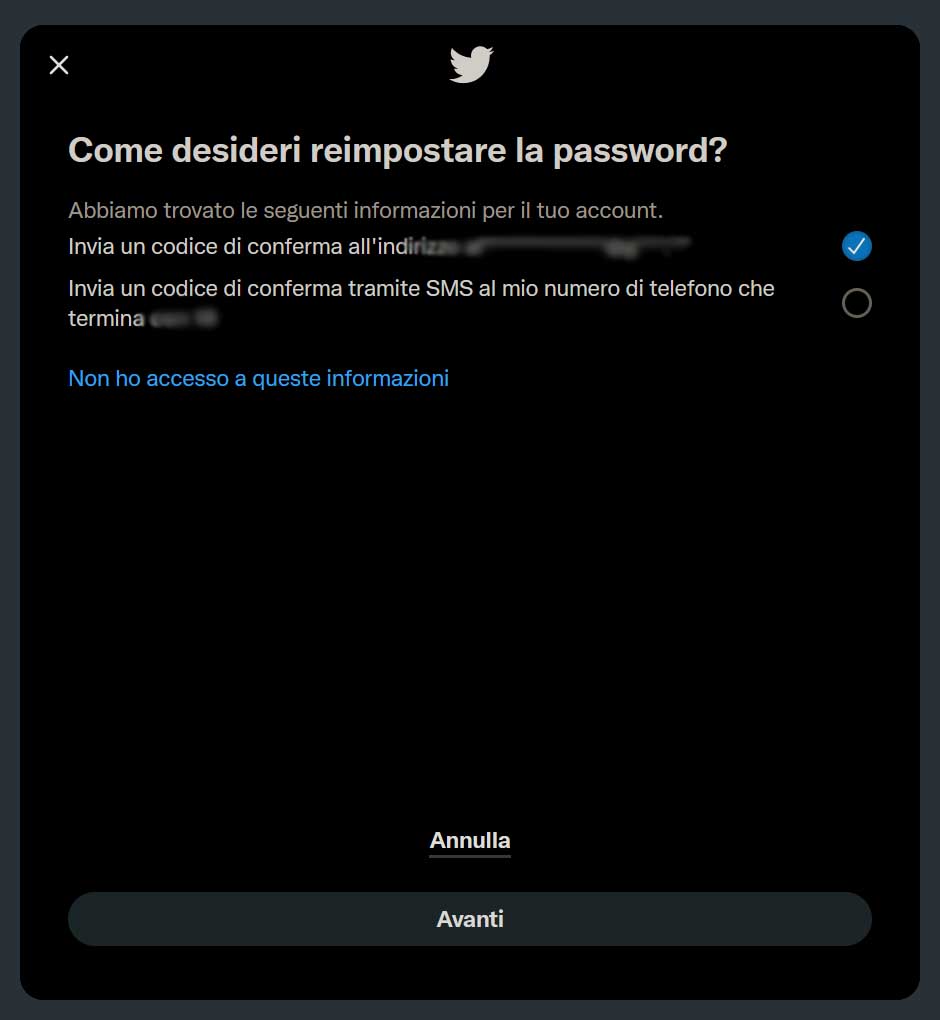
You will soon receive an email that looks like the one below.
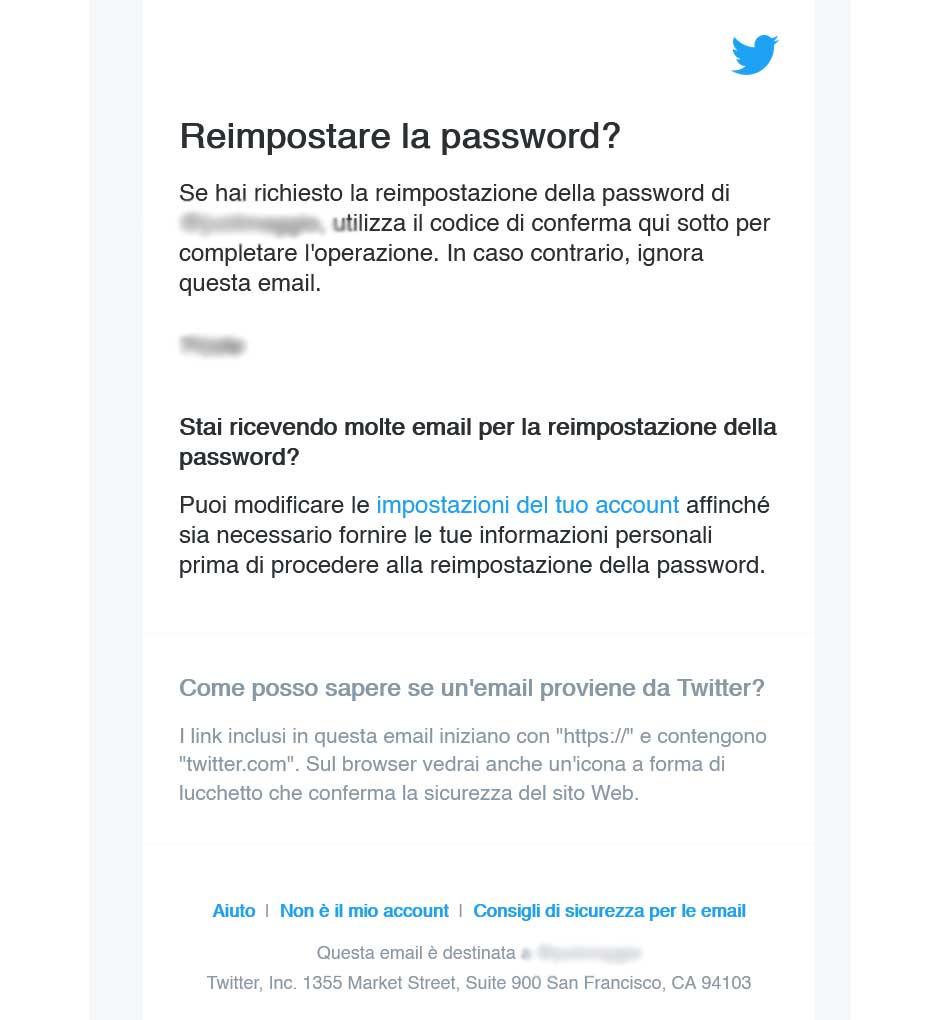
Modifying the Phishing Email
With the previous step, the hacker received an original email from Twitter and he is ready to change it. By modifying this email, the hacker can make it into a malicious email that can use to hack Twitter accounts.
Doing that is extremely simple, he would just need to open the email with Microsoft Outlook or Mozilla Thunderbird and click on Forward. At this point, he can edit the text in the email how he pleases.
A common approach hackers use when trying to hack Twitter accounts is to say the account has been compromised and a password reset is needed immediately. The typical phishing email would look a lot like the one below (note that this has been created with Outlook).
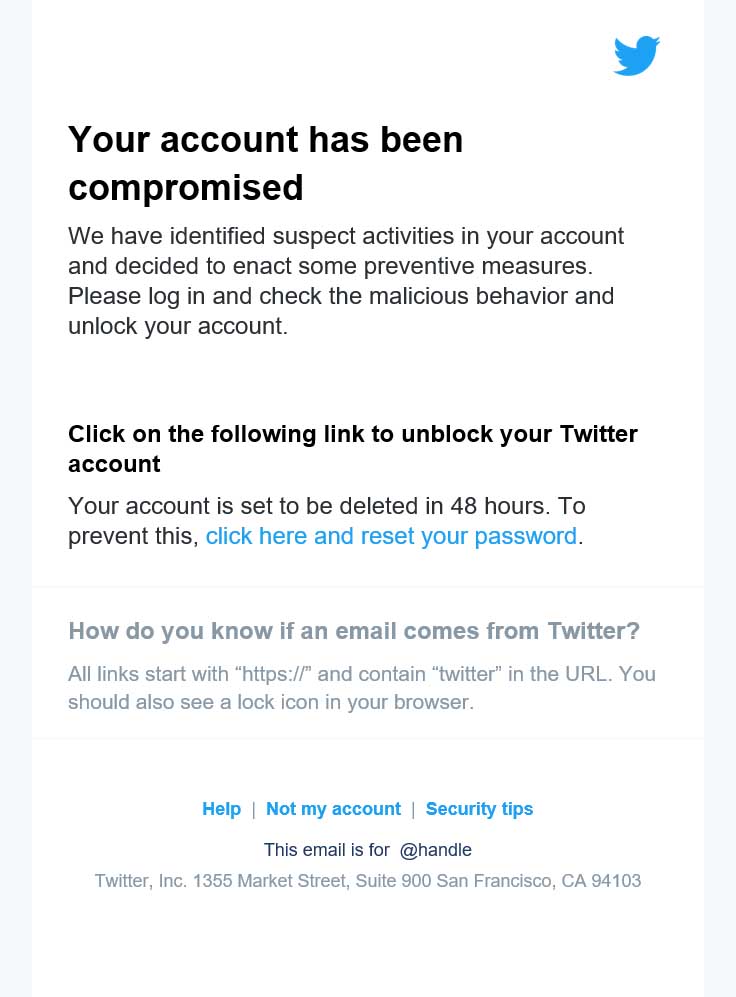
However, changing the text is not enough, for the phishing email to do something it must redirect to a malicious URL that can steal password. The hacker knows this, so he will also create a malicious website, and then change the link in the email to point to that website.
Of course, the phishing website is an integral part of hacking Twitter accounts, so this is what we will address next.
Malicious Websites
The malicious website is the thing that is actually in charge of “stealing” the user’s password. Hackers will typically setup websites that look a lot like Twitter and ask credentials to login, but in reality, they will just log those credentials in a file that the hacker can access and see.
Even if creating a malicious phishing website is a little harder than just a phishing email, it can still be done by almost everyone. This is because the website has only two components: the presentation and layout, that looks a lot like Twitter, and a simple script to save passwords.
The first step is to clone the HTML code from the Twitter login page. This can be done with a Website Downloader tool or extension for Chrome or Firefox. As sometimes these tools don’t work, you can just use the Developer Tools in your browser to inspect the page.
Copy the page code on your computer and change the action when the form is submitted to call a “dumper.php” script that we will create soon. At the moment of writing this, it is not so easy to do that for a new hacker because Twitter is not using standard HTML forms anymore, but rather they rely on custom JavaScript code.
Nonetheless, the implementation that you need to do if you are familiar with JavaScript would be, when the user puts the password and clicks next, to send that information in a POST request to /dumper.php. Then, the content of dumper.php should be the one below.
// Dump the request to a file
$req_dump = print_r($_REQUEST, true);
$fp = file_put_contents('credentials.txt', $req_dump, FILE_APPEND);
// Send the user to real Instagram
header('location: https://twitter.com');This will save all the passwords in a text file and redirect the user to the real Twitter afterwards, so that he can remain unaware.
The only remaining step is to upload dumper.php and all other HTML files you used to replicate twitter in a hosting platform, and there are many free hosting platforms out there. If all of this is confusing to you or if it is your first time, don’t worry – check this guide on how to hack IP addresses, it will explain how to create a malicious site in detail.
Protect Against Twitter Hackers
With all we mentioned before, it seems trivial that hackers have an easy way to your account and that you will never be safe. In some sense, they have, but there are good ways you can protect yourself and reduce the chances of being hacked significantly.
There is one big thing you can do counter people who hack Twitter, and that is Two-Factors Authentication, or Multi-Factor Authentication (MFA) in general. That is, enable features that require to confirm any new login or action on your phone or via SMS. In this way, even if the hacker gets your password, he can’t do anything with it unless he gets access to your phone as well.
Beware, hackers can get access to your phone as well, but you would need to be a victim of a targeted hack, that is, the hacker wants to hack specifically you. Phishing emails are often targeted to as many people as possible to see who falls in the trap.
Other Ways to Hack Twitter
Hackers do not limit themselves to hack Twitter accounts, but they do also other things. Another common hack is the “like farm”. Hackers set up entire rooms full of physical phones, each with Twitter installed and a fake account in it.
These phones are always in charge, plugged in and turned on, installed on racks so that the hacker can see them. They are the cheapest phones possible, because the hacker wants as many of them as possible. He installs a click bot software inside the phones, so that it can programmatically control many accounts, having them like things, write and reply to tweets, and so on.
Of course, this is completely against Twitter’s policy. Yet, hackers can go even beyond that with a creepy twist by using zombie farms. A zombie farm is a set of many devices that are actually normal devices owned by other people. The hacker gained somehow access to them, and while the person is using his phone normally, the hacker is controlling it in background to make it do weird stuff on Instagram. This is also significantly illegal.
Hack Twitter in Summary
In this brief guide we saw that people can hack Twitter fairly easily, but that you should also have ways to protect yourself. We saw that the most common things hacker can do to hack Twitter are:
- Steal an account with phishing
- Collect more followers with phone farms
- Collect more followers with zombie farms
This has been a simple and short guide and cannot be exhaustive, hackers can do many more things than that. If you are serious about hacking, why not considering learning more about it? Check out this article on how to hack IP addresses to continue learning. You may also want to read how to hack Instagram or how to hack TikTok.
