Preparing attacks to systems and networks is complex. Yet, all the attacks starts from the same point: reconnaissance. This aims to understand how the system works, and what are possible vulnerabilities. Several tools allow you to perform reconnaissance, but the most famous is nmap. Even if you don’t want to do penetration testing, you should know how to use this tool. In this nmap tutorial, we will see how to use nmap and its visual companion, zenmap.
Introducing Nmap
What is Nmap?
Nmap stands for “network mapper”, and this is pretty explanatory. In fact, nmap is a tool that allows you to create a detailed map of a network. As we will see later in this nmap tutorial, you can use this tool to have a clear picture of the network. To start, we can reconstruct the topology, identifying all the devices in the network. However, nmap can do far more than that. Using advanced techniques, it can identify what services are running on each host and even their version. If you are lucky, nmap will even detect the operating system of each device.
Knowing services, versions, and operating systems is essential for the attacker. With this precious information, he can use targeted attacks and exploit known vulnerabilities.
Nmap is a command-line tool. In the terminal or prompt, you can use the nmap command to launch the scan. In this nmap tutorial, we will see how to use options of this command to better control the scan.
What about ZenMap?
ZenMap is a graphical interface to facilitate the use of nmap. With zenmap, you can construct nmap queries easily, and run them from a graphical interface. However, its best enrichment to nmap is about the output. ZenMap can actually visualize the topology of the network graphically, and you can click on each host to gather more information.
Where to get nmap and zenmap?
If you are a Microsoft Windows user, you can download the binaries from the official nmap website. These are the executables that will install both nmap and zenmap. Once you install them, you are ready to use nmap in the prompt, and you can search for ZenMap within your installed programs. Luckily, both nmap and zenmap are free and open source!
For Linux users, using your package manager is enough to get you running. Depending on your Linux version, you can run sudo apt-get install nmap or yum install nmap. If you want zenmap as well (as you should), go to the official website of nmap.
Mac users will find executable binaries in the same link of Windows users.
Nmap tutorial: scanning with nmap
A first scan
Despite its immense power, using nmap is simple. This is especially true for basics scans. In fact, the syntax for the command is just this:
nmap [scan type] [options] {target}Scan type and options are in square brackets because they are optional. By default, you only need to specify the target. After all, you need to tell nmap what you want to scan! The official nmap community offers you a sample target website to scan: scanme.nmap.org. If we scan it, we will see this output.
C:\>nmap scanme.nmap.org
Starting Nmap 7.60 ( https://nmap.org ) at 2018-05-12 11:45 W. Europe Daylight Time
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.22s latency).
Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp open ssh
53/tcp filtered domain
80/tcp open http
445/tcp filtered microsoft-ds
9929/tcp open nping-echo
31337/tcp open Elite
Nmap done: 1 IP address (1 host up) scanned in 78.17 seconds
C:\>As you can see, this will tell you the destination IP as well as the opened ports with the service they expose. In the last line, it tells us that one host is up. This is because we can target multiple hosts or even entire networks at the same time. A common approach is to target an entire subnet, in CIDR notation. For example, try using 192.168.1.0/24 as target (if your home router offers that network). This will scan all hosts in that subnet, identify which ones are up, and the exposed ports on each. You can also specify an IP range, like 172.16.10.43-172.16.10.53.
Nmap offers endless possibilities
In case you omit the target, nmap will show the help. Here you will see that you have literally tons of options to play with. You can detect IPS and IDS systems, detect the target operating system, and more. Covering all the options is way beyond the objectives of this article, yet we are going to see the most common options.
Knowing some options will allow you to quickly get the information you need. Doing a scan can take time, so you don’t want to scan for something you already know you won’t need.
Nmap options for Host Discovery
Host discovery is the first thing you do with nmap. That is, you look for the hosts actually listening within a broader range of addresses. This is the first step to identify interesting hosts. Here, you have several options to help.
-sLjust lists the hosts, and attempt a reverse DNS. This means you will get the name of the host from its IP, if available. This is a quick starting point and does not send any packet to the target host. Thus, it also disables more advanced features.-sndisables port scanning, and just discover the hosts. However, port 443 and 80 are checked with a TCP SYN during the host discovery process. This comes handy if you want to discover many hosts in little time, as port scan takes time.-Pndisables the first discovery step, that identifies if a host is up. By default, nmap will perform advanced (and long) scans only against up hosts. If you use this option, it will attempt the full discovery against every single host.-PSattempts the discovery using TCP SYN against a port range-PUattempts the discovery by sending UDP packets to the specified port range-POis for advanced users, as it attempts the discovery with raw IP packets, setting the protocol payload in IP header to the protocols specified. This will look for any kind of response with the same protocol, or for an ICMP protocol unreachable message-PRis for ARP discovery, and very important for LANs. If you are attempting to discovering hosts in a LAN, if they respond to ARP you will know they are up. Useless on remote hosts.--tracerouteperforms a backward traceroute to the host. It starts with a high TTL and decrements until zero. This allows nmap to perform some efficiencies.
Port Scanning
Once you discovered the hosts, the next step of this nmap tutorial is the port scanning. This allows you to identify what each server is doing in the network. We know that applications use generally TCP or UDP, and each application has its own port. (If you are curious about that, I recommend this reading on TCP and UDP).
Nmap classifies each scanned port with a state. If the port is open, there is an application actively listening on that port. Instead, if the port is closed it responds to Nmap probes, but no application is listening. If the port is unfiltered, nmap can access it but was unable to determine if it is open or closed. The port could also be filtered: an intermediate device is preventing nmap from accessing it. The other two states are open or filtered, and closed or filtered: when nmap is unsure if the port is filtered or either open or closed.
Manage the port scan
Now that you know the basics, we are ready to look at the options to do port scanning.
-sSis the default TCP SYN scan. Since you don’t open a full TCP connection, this is known as half opening. Nmap will send a SYN message and wait for a SYN+ACK. If that arrives, the port is open.-sT, unlike-sS, attempts a full three-way handshake. This takes more time, but it is the only option if you are not running nmap as an administrator.- –
sUis for scanning with UDP. While most services are based on TCP, this is important for UDP-listening services like DNS or SNMP. Since UDP does not have a reset or standard reply message, you may not get a response even for ports that are actively listening. In that case, you will see anopen|filteredstate for that port. -sAis a TCP ACK scan, and it only sends an ACK message. It does not determine port opening but allows you to detect firewall rulebase. Thus, it detects if the port is filtered or not.--scanflagsallows you to specify the value of each TCP flag for your scan.-ballows you to exploit an FTP server to make it do scans on your behalf. This leverages a feature of FTP that can be exploited on many levels. Thus, many FTP providers dropped support for it.
Better targeting for port scanning
In the previous part of this nmap tutorial, we saw how to tune the port scanning process. However, we can also specify what ports we actually want to target, and a scan order. Take a look at the following options…
-pis the most basic one. In fact, this allows you to specify the port range to check.-exclude-portsis the opposite of-p. This allows you to define what are the ports you wish to not target.--top-ports <n>is an interesting option. Nmap has statistics about the most commonly open ports, and this will attempt a scan to the top “N” ports only, that are generally open.
A deeper scan
Our next step in this nmap tutorial is to gather more useful information about each target host. Nmap can detect what service is actually running behind a port, and even detect the OS based on common services each OS exposes.
To do that, nmap has a database of queries to stimulate a response from the target host, and know how to parse the responses. Nmap can use such responses to extract precious information. All of this involves complex algorithms and a lot of data to work with. However, despite the complexity, we can turn this on with a few options.
-sVenables version detection for all target hosts-o, instead, enables operating system detection. OS detection is also included, among other things, in-A.
Of course, there are more options to finely tune the detection. Yet, with these two options alone you are good to go, as they will provide all the information you need. In fact, nmap is smart enough to do things in the best way, and you need to tune additional parameters only for advanced users.
How to use nmap
Launching the command
At this point in this nmap tutorial, you know how to launch nmap from the prompt. In fact, you also know the options to make nmap respond to your needs. However, there is a quick syntax act you can use. While using it is not necessary, knowing it is mandatory if you want to understand some online tutorials.
In options like -sS, you are actually telling two things to nmap. The first is that you are defining an option for scanning (-s). The second is that, among other scanning option, you want to use TCP SYN (S). You can use a single -s to combine multiple options: -sS -sV can be written as -sSV.
For this nmap tutorial, we are going to analyze a sample nmap output. To generate it, we used this command:
nmap -T4 -vv -sAV nmap.orgThe option -T allows you to specify how fast the scan should run, from 0 to 5 (fastest). Instead, -vv indicates we want the max verbosity. This will tell you what nmap is doing while it is doing it.
Analyzing nmap output
Below, the output from the command we executed in the previous example. We run that with administrative privilege, to get the best out of nmap.
C:\>nmap -T4 -vv -sAV nmap.org
Starting Nmap 7.60 ( https://nmap.org ) at 2018-05-12 21:42 W. Europe Daylight Time
NSE: Loaded 42 scripts for scanning.
Initiating Ping Scan at 21:42
Scanning nmap.org (45.33.49.119) [4 ports]
Completed Ping Scan at 21:42, 0.73s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:42
Completed Parallel DNS resolution of 1 host. at 21:42, 0.01s elapsed
Initiating ACK Scan at 21:42
Scanning nmap.org (45.33.49.119) [1000 ports]
Completed ACK Scan at 21:43, 13.73s elapsed (1000 total ports)
Initiating Service scan at 21:43
NSE: Script scanning 45.33.49.119.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 21:43
Completed NSE at 21:43, 0.02s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 21:43
Completed NSE at 21:43, 1.47s elapsed
Nmap scan report for nmap.org (45.33.49.119)
Host is up, received echo-reply ttl 52 (0.21s latency).
rDNS record for 45.33.49.119: ack.nmap.org
Scanned at 2018-05-12 21:42:52 W. Europe Daylight Time for 18s
Not shown: 993 filtered ports
Reason: 993 no-responses
PORT STATE SERVICE REASON VERSION
22/tcp unfiltered ssh reset ttl 52
25/tcp unfiltered smtp reset ttl 52
70/tcp unfiltered gopher reset ttl 52
80/tcp unfiltered http reset ttl 52
113/tcp unfiltered ident reset ttl 52
443/tcp unfiltered https reset ttl 52
31337/tcp unfiltered Elite reset ttl 52
Read data files from: C:\Program Files (x86)\Nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.61 seconds
Raw packets sent: 2004 (80.152KB) | Rcvd: 17 (676B)First, it tells you that it is loading the Nmap Script Engine (NSE) with 42 scripts. Nmap automatically loaded some useful script to achieve what we wanted. In then launches the scan, which is very quick since we have just one host. You will then see the reverse DNS (rDNS) record for the IP, and the ports open on this server.
As you can see, they are all unfiltered as nmap received a reset in the TCP connection (you see that in the reason column).
How to use ZenMap
Launching the scan
ZenMap is nothing more than a GUI running on top of nmap. If you launch it, you will end up with a big white screen where you have a bar on the top to structure your nmap query. You can specify the target and choose from a set of pre-defined scans. Using these two boxes, ZenMap will dynamically build the nmap query on the larger box. In the example below, we selected an intense scan for nmap.org, and this translated into nmap -T4 -A -v nmap.org. You can edit all three boxes.
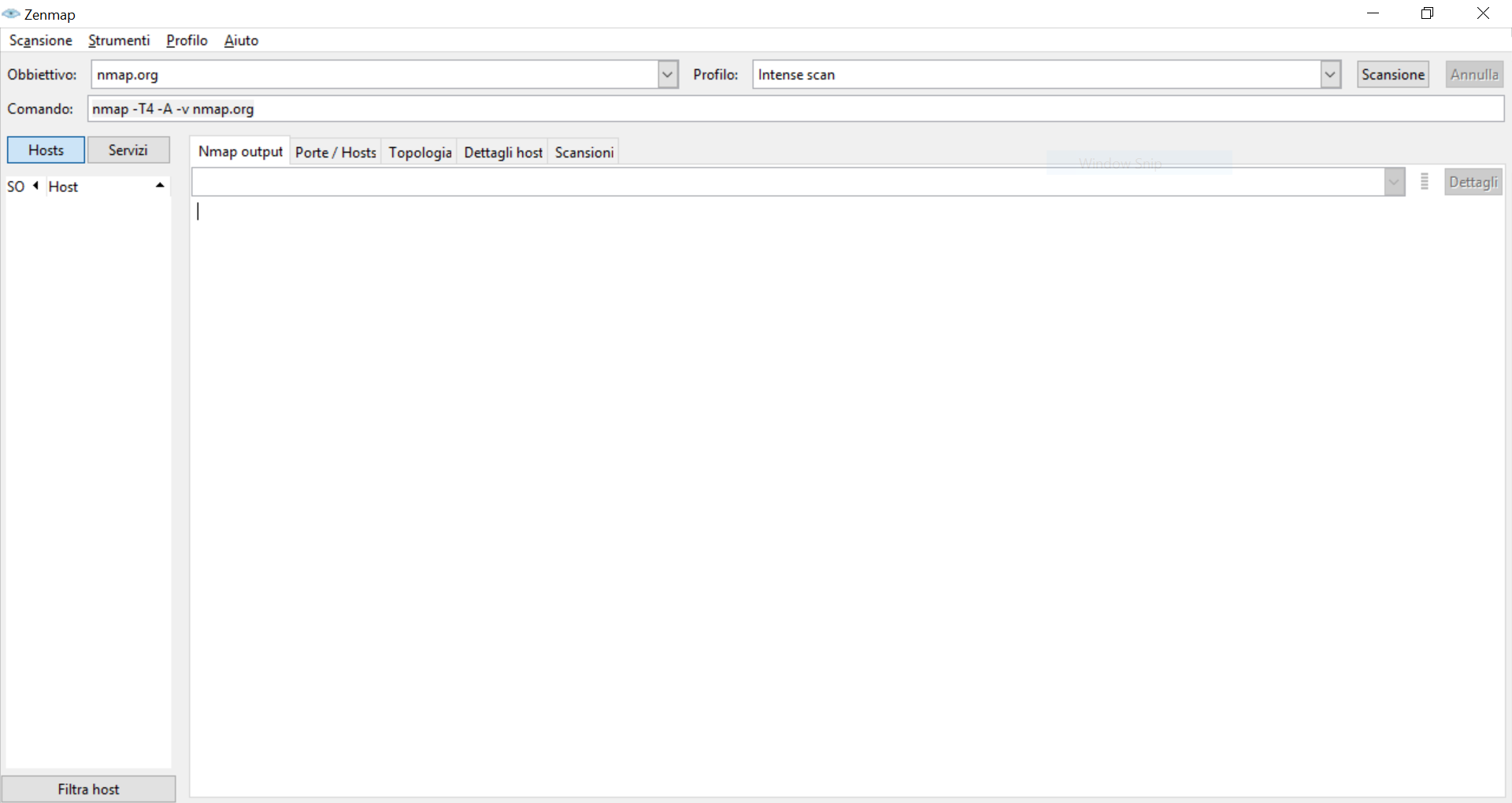
Once you are ready with your query, it the Scan button on the top-right.
Looking at the output in ZenMap
This is where ZenMap overcomes the limits of nmap CLI representation. As you launch the command, you will see the CLI output from nmap in the blank panel at the center of the screen. While nmap discover hosts, they will appear on the left panel, and you can click them to see all the gathered information of each. You can also directly list services, instead of hosts, in the left panel. This is what you see when the scan finished.
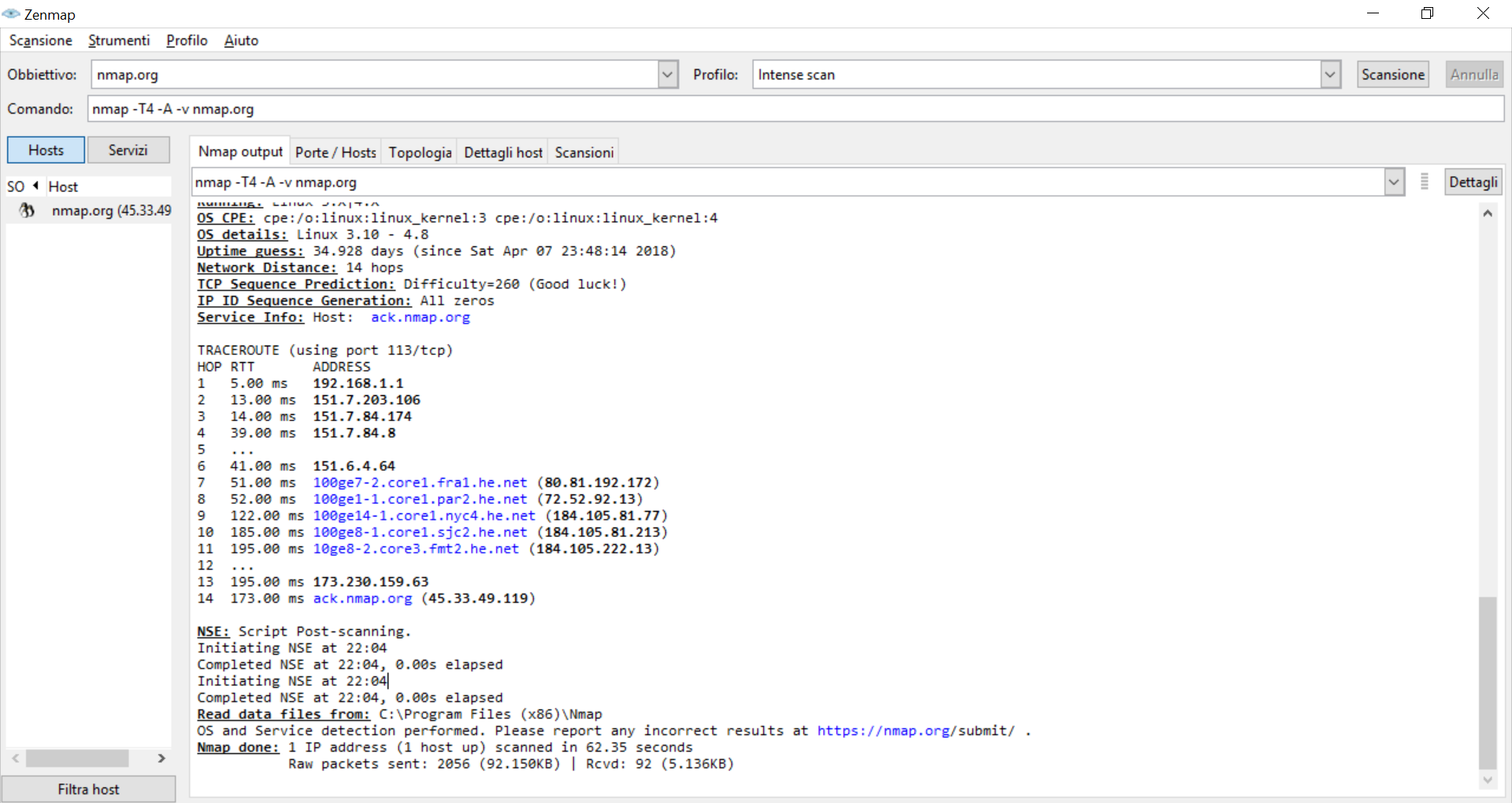
As you see, in the main panel you have several tabs to switch between. Feel free to experiment with them, but the most useful is the topology one. This will create a visual representation of the network, making it easier for you to understand what is where.
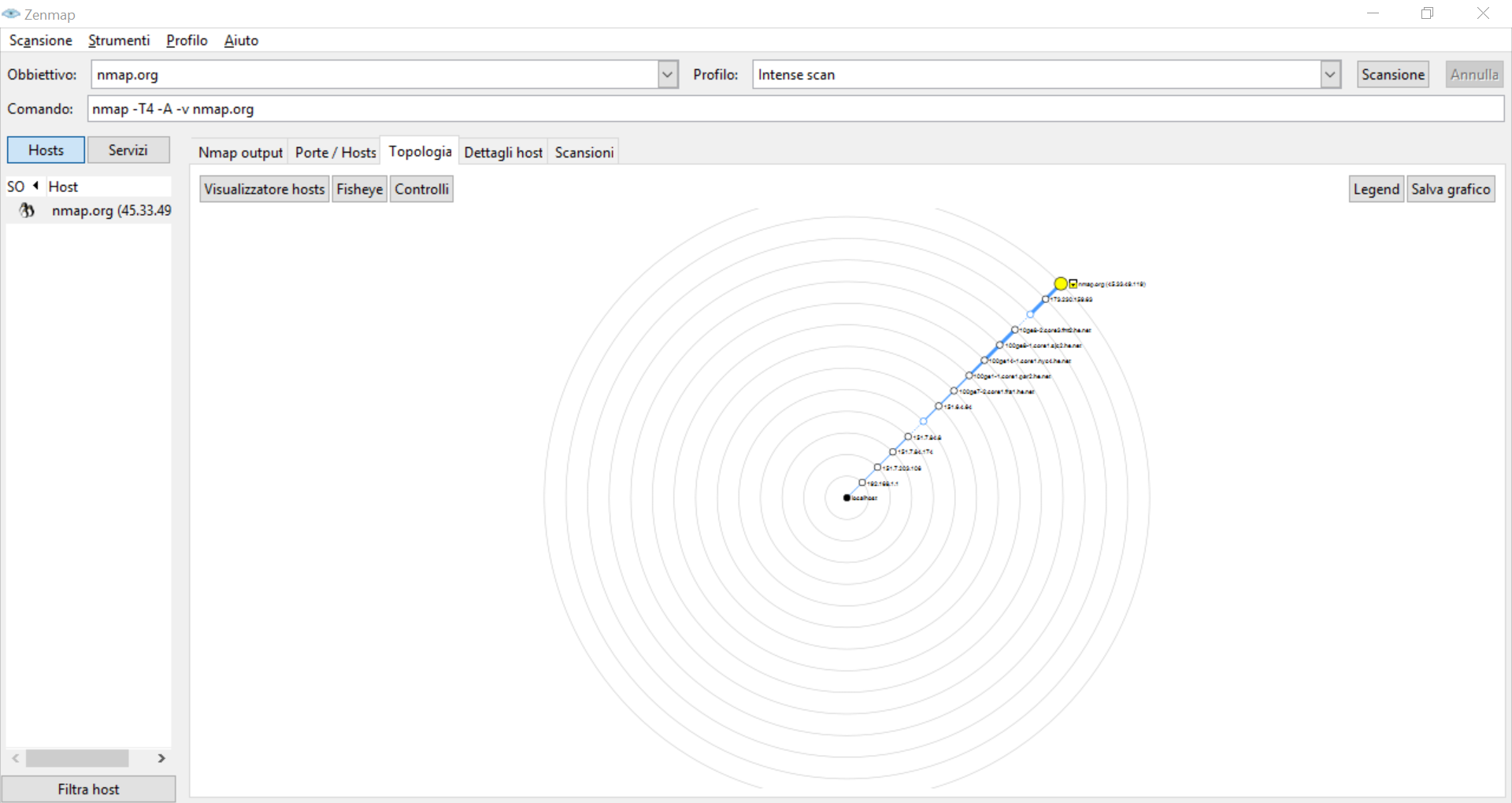
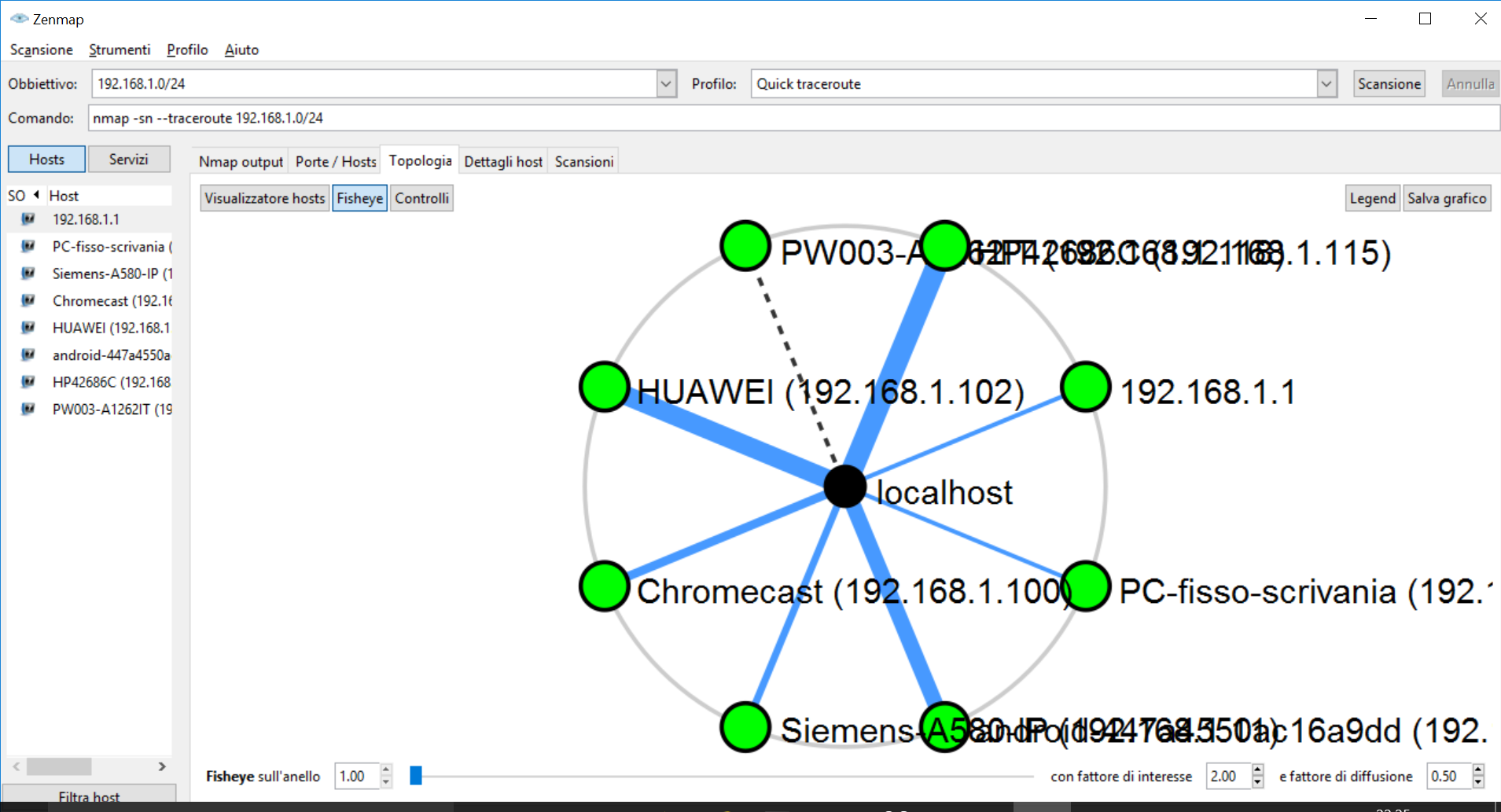
Of course, this becomes dramatically useful if you are scanning a subnet or multiple subnets. When scanning a single host, it has still relevance as you can see details about the trace. For example, not all links between hosts are equal: some may hide additional hosts! Be sure to check the legend when looking at this chart.
Wrapping it up
Congratulations! At this point, you have an intermediate understanding of both nmap and ZenMap. With this knowledge, you can start reconnaissance attacks in your penetration testing activities, or simply do a better network inventory. Sometimes, you will probably use nmap to troubleshoot if a server is listening on a given port.
What do you think about nmap and its strengths? What are you going to use it for? Let me know your thoughts in the comments!
