Password cracking is one of the most important branches of hacking. If you know a password, you can access the private information it protects. Thus, hackers dedicate a lot of effort trying to discover passwords, and password cracking does just that. If you want to learn how hackers may crack a password, you are in the right place.
What is Password Cracking?
What is Password Cracking?
Password cracking means identifying a password by using hacking tools and software. In fact, a hacker has many ways to obtain a password, for example phishing (asking the password directly to the user who knows the password, disguising itself as a legitimate website). Yet, password cracking is different, and can be defined in two broad branches.
- You have the hash of the password, and you want to find out the original password (more on what is an hash later)
- You don’t know anything about this password, and you brute force it (try to guess it many times)
In this guide, we will see both types of attacks, as they are bot valid to crack a password. However, we will focus on password cracking rather than brute forcing.
What You Need to Know about Hash?
What do you need to know about hashing for password cracking? Fortunately, just the basics, and we will explain them right here.
Let’s start with the most basic thing, a definition of hash and hash function. A hash function is a unidirectional function that takes some text and transform it into some other text. It is unidirectional because you can get to the end result from the original text, but from the end result you can’t get back to the original text. So, it works only in one direction.
Most importantly, the same input as original text will always produce the same end result. This means there is a 1-to-1 mapping between original text and final result. The final result is the hash, specifically the hash of the original text.
Why is this important? Because passwords are stored in hash. No well-made application will store password in clear text as they are, otherwise, anyone accessing the database can read all the passwords of all users and then log in as any user. Instead, passwords are stored in form of hash, so that even if you were to read the database, you wouldn’t be able to get a password you can use to log in on behalf of a user.
How all of this works? Every time you attempt to log in, you enter your password, and the server that you are accessing (e.g., Facebook) computes the hash of the password. Then, it compares it with the hash in the database, and if they match it means you have inserted the proper password, you are clear to log in.
There are many functions that do hashing, but most notably there are MD5 (not secure, should never be used for passwords anymore) and SHA256 (the current best practice as of 2022).
Password cracking is about retrieving the original password starting from the hash.
How to do Password Cracking
John the Ripper
John the Ripper is not a person, it is actually a software that can be used to crack passwords. It is free and open source, and you can download it from here. It is available for Linux, Mac, and even Windows, making it a convenient solution to crack passwords.
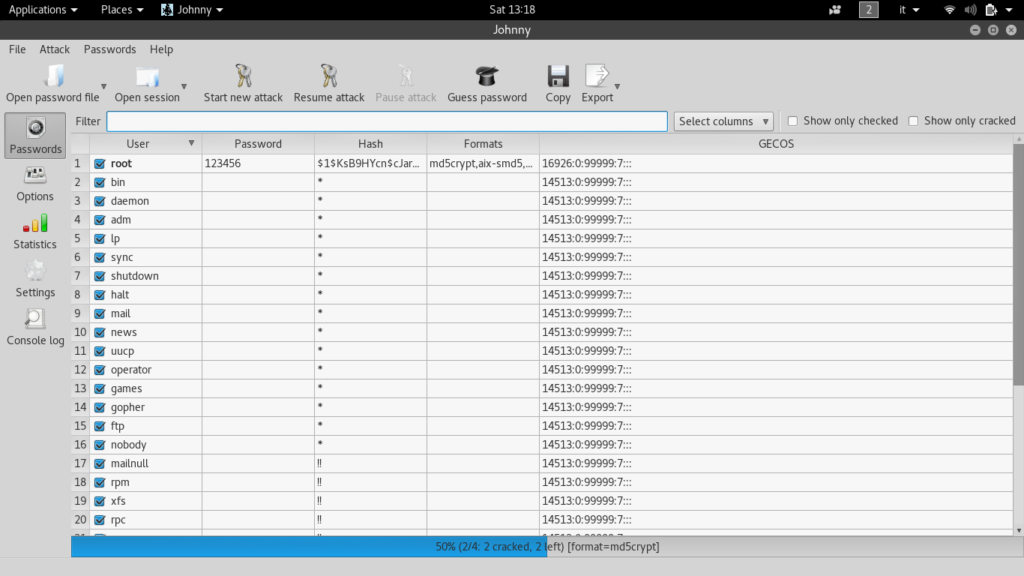
This software takes care of everything, you just input some hash and it will try to brute force its way trying different passwords and checking if the hash obtained is the one you have. It can be the best one to crack the passwords of a Linux system, of which you can see the hash in the file named “shadow”. On a Linux system, do the following command.
cat shadowThen, input this data into Johnny (we are starting to get very friendly with this tool) and let it do his magic.
Rainbow Tables
Rainbow tables are another great tool to do password cracking, and they tend to be faster than “stupid” brute force. We won’t get much technical, but hash functions uses table and perform various iterations and permutation on the data to go from the original text to the hash. A rainbow table can be seen as an intermediary table used in a middle step. Since we are only running up to a middle step, and not all the way to the end, we can save a lot of time.
Of course, this is an oversimplification, but nowadays you don’t need to be a master of cryptography to do password cracking. In fact, you only need to install rainbowcrack (Linux only at this time).
To install it, run:
sudo apt install rainbowcrackThen, to crack a single hash, use
rcrack . -h <your hash here>Dictionary attack
One of the fastest attacks in password cracking is a dictionary attack. The idea is simple: computing the hash of a text takes times in the CPU. Instead, looking up in a database is much faster. So, the idea is to create a database of hash and associate each with the text that creates it.
In this way, you create the hash database once and then the lookup is fast. You only need to know the hash, and if is in the database you will get the password that generated it immediately. The only challenge with this is that the database, the dictionary as we call it, can occupy huge amount of space.
In addition, salts (more on this later) can make this attack completely useless. And, as you can imagine, modern applications that implement best practices use salts.
Custom Brute Force
Sometimes, password cracking gets really nasty. In fact, there are cases where the hacker does have the hash of the password because it is in a protected database or because of a salt mechanism (more on this later). In those cases, the hacker can resort to try cracking directly the application that holds the password.
To do so, the hacker will create a custom script that generates one potential password after another and attempt to use that to connect to the application. If the application is a website, it can easily be done with a python web scraper (a script that can surf the web and input text into forms).
One thing that must be considered here is that application tend to rate limit connections, so the hacker will have quite a hard time because he can try just so many passwords per minute. Hence, he needs to be careful at the potential password to try, avoiding passwords that are unlikely to be used.
Protect From Password Cracking
How to Protect from Password Cracking as a User
Password cracking takes time because the hacker needs to try all potential combinations of passwords. The longer your password, the better.
Originally, password recommendations told you to add as many different types of characters as possible in your password and change it often. A more current recommendation is to use an extremely long password, even if it contains only text and numbers, and keep it for a while. Of course, you don’t want to use an easily guessable password like a phrase from a song.
In addition, no matter how strong your password, it will never be enough. Instead, use multifactor authentication (the OTP on your phone) whenever possible.
Salts
Salts can protect an application from some password cracking methods, especially dictionary attacks. In the normal case, as owners of an application, we store the hash of the password in the database. With salt, this changes.
We store a salt, which is a random string, typically long (128 characters for example) and the hash of the salt plus the password text combined. In other words, it is like the original text of the password also contains the salt.
In this way, the hashed text will be so long that would make unfeasible to have a dictionary with all the possible combinations, making dictionary attacks useless.
Password Cracking in Summary
In short, password cracking is the field of hacking that recovers password from hash strings. It is an important field in hacking because it allows hackers to access private information. This is done mostly through:
- Johnny the Ripper
- Rainbow Tables
- Dictionary attacks
- Custom brute force attacks
If you want to learn more about another pillar of hacking, you should check out this article on how to hack IP addresses.
