If you think that hacking is all about programming and complex commands, think again. While complex technical stuff is a key part of hacking, most times this is not the way to go. Violating a system can require a huge efforts, and not all hackers will have the power to do that. However, with social engineering they can get what they were looking for – often times without violating the system. If you don’t know about social engineering, or just know the basics of it, this article is for you. It will show how this can impact companies of all sizes, and how to protect yourself.
What is Social Engineering?
To be short, social engineering is the art of hacking people. While this definition is accurate, it doesn’t really give you an idea about what social engineering is exactly. However, the definition must be so vague as social engineering is vast. We can say that because social engineering has no rules.
With this approach, the hacker misleads people into giving him sensitive information. This makes this discipline much different from traditional hacking. Here, you don’t have protocols to study and exploit. You are not searching for bugs in software. Here, your target is the human brain. Thus, the hacker doesn’t have a mathematical formula to do the attack. Sometimes, the attack may work, some other it just won’t. Not all people react the same way, and not all attacks are great for all people.
Until now, we have seen that Social Engineering is all about violating people. Because of that, it doesn’t have a simple or reproducible formula. This doesn’t mean social engineering must be different every time. There are some attacks that work most of the time, and hackers love them. They adapt to customers, small and big companies with some simple tuning.
Some common approaches
Phishing
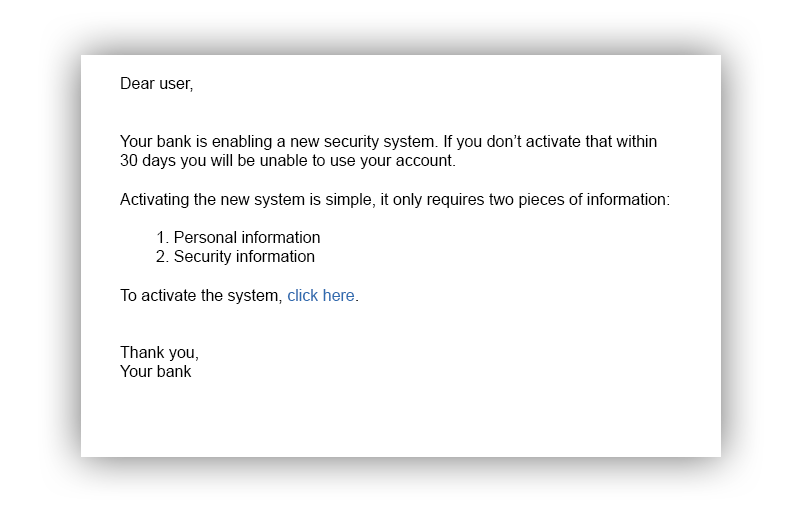
You might have heard this word. If you have been using the Internet for a while, chances are someone tried to scam you with phishing. This attack is simple, the hacker claims to be someone else. More than that, the hackers claims to be someone (or some company) you trust and ask you to provide your information. Common techniques include:
- Email contact with a trusted company’s logo
- Fake website resembling a trusted company’s website
- Phone calls and snail mail are also common in this scam
Luckily, anti-SPAM systems gets better and better and email are not a real issue anymore. A few years ago, these attacks were common in the customer’s environment. Individual person got attacked daily, and many of them got scammed in the end. As users started to understand these were attacks, hackers got better and better.
A phishing attack that actually works
Phishing is the simplest social engineering attack, since you are explicitly asking the user to give you sensitive information. However, this involves some kind of trust that the user must have in the attacker. Performing a successful phishing attack is all about gaining trust. As in many cases, the best way to do that is to show the user you know them.
Phishing attackers send mails referring the user with his name, they add their account number and some sensitive information to convince the user they are who they claim to be.
Phishing in the Enterprise
In an enterprise, you cannot cold-call an employee asking for sensitive information. This is simply because it won’t work. However, this doesn’t mean phishing attack are not effective in enterprises. They happen all the time, but not in the traditional manner. Here we have a few example.
- The attacker calls claiming to be a colleague from a branch in another country, asking for information on a contract you are working on
- He claims to be a new employee of a supplier or a customer
- The attacker may claim to be a friend of an existing customer requiring similar services
Even there, hackers are expert. They will use your name, and the name of your colleagues, supplier and customers. Their request will sound legitimate, except that you have no way to tell they are what they say, beside trusting their words.
Defending yourself is not easy, but…
If you handle IT or security in a company, the best you can do is to inform users. Tell them to be careful, and you will reduce the threat. Some times, this is not enough anyway.
The Cleaning Company
I remember an interview with John McAfee, founder of the antivirus company. The interviewer was claiming that McAfee had some kind of special tools to do penetration testing. Instead, John repeatedly say no. The interview was taking a bad direction, so McAfee said something like that:
No, we don’t use any special tool. You just go there, say you are the cleaning company, the electric company – whatever. Then you plug your device to the network, and you are in. This is it.
And this is really it. How many companies bother turning off all unused ports? You just find a wall outlet and you are ready to go. While companies may enforce protection from outside attacks, they are not so well protected against attacks coming from inside. Hackers know that, and this is why they directly try to go inside.
This is why hacking is as easy as plugging a cable. Literally.
How to protect?
Protecting from this attack is easy. After all, no user is giving out sensitive information: an unauthorized user is accessing the network. As you can see, the solution is enforce an authentication policy to anyone connecting to the network. This is not just like a Wi-Fi password, this is individual authentication. Each user will have his own credentials.
To implement this kind of authentication on switch ports, we need Network Access Control – NAC. To do that, we can use a standard protocol: 802.1x. Chances are, your switches already support it. You only need a server to grant or deny access.
Will NAC save me?
Almost. NAC is seriously a game changer. But this doesn’t mean you are protected by simply using it. Teach users to lock their computers whenever they go away. The “cleaning hacker” may come in, see a PC and start looking for sensitive information for it. Even better, they may install a virus from a USB stick and there you go. They will control that PC.
Money doesn’t buy happiness, but access instead
This is the last resort, yet someone really trying to violate a company will try it if the above methods failed. Fortune said it all loud: one in five employees would sell their credentials. In their article, they show a research they did on a pool of users – one in five is willing to sell their credentials to access the corporate network. This is serious stuff, yet 44% of them were willing to do that for less than 1000$.
We all know that 1000$ won’t change our lives, yet people will still do something illegal for so little money. Why? Because users do not realize the importance of their credentials. They do not realize what things a hacker could do once he accesses the network with the credentials. Thus, why not? 1000$ is better than zero after all.
We all have a price
For this attack, there is no solution. You can inform the users and tell them how important and confidential their credentials are. In the end, you will only increase their cost. Any competitor willing to bring on the table hundreds of thousands of dollars will have the credentials, most likely.
Do you think no one would pay so much for just having some credentials? Imagine all the intellectual property and sensitive data a multinational company may have. They could be worth billion, and someone might want to steal them. Furthermore, we are talking about something that is probably illegal world-wide. If they don’t pay you, I bet you won’t call the police…
The USB stick
Leave a new 128GB USB stick near the entrance of a company. It won’t make it to lunch. In fact, someone will take it and probably plug it inside office’s PC. They shut down Iran power plants with this type of attack.
If a company develops some kind of USB control, this attack may fail. Not all companies do that, and this exposes them to serious threats. The USB may contain a virus that allows remote control of the PC, and that is able to spread inside the company.
The Play of An attack
Now that we have seen some types of attacks in Social Engineering, it is time to see how they can be glued together. Hackers always have a specific purpose, and they get there by combining these attacks. Combinations are endless, but here we will present you an example.
- With the “Cleaning company” attack they get access to your company. This is done in remote branches, where security is not enforced so heavily as HQ.
- Once they are in, they plug a device into the network. Even a Raspberry PI will do.
- Then, they perform a DHCP Starvation attack. Basically, no PC will be able to navigate unless they say so.
- Once the DHCP server is KO, they act as rogue DHCP server – telling PCs on the network what to do in order to navigate. They will of course tell PCs to pass through them.
- Now all traffic passes through them, and they can sniff it.
- Chances are some internal services are HTTP – not encrypted. They will get sensitive information by just listening.
And at this point, they can do whatever they want with that information. If you want to read more about DHCP attacks, read this article about them (and how to protect yourself).
Conclusion
Social Engineering is the easiest hack in the world. It existed before computers, and it will always exist. Thus, hackers will try to leverage it before trying any other technical or advanced attack. To protect yourself, teach the users how to defend themselves, and invest in a system that can monitor users activity.
What do you think about social engineering? Have you ever thought how easy is to hack? What are the techniques you know about? Just let me know in the comments!
