As a network engineer, you are probably going to work with switches quite often. Switching is the master technology of the data center, and of the enterprise. Unless you work within a service provider, switching is what you are going to see every day. Therefore, you need to know very well the technologies related to this domain of networking. Most importantly, you need to integrate them together, as part of your job. In this skill integration lab, we test you for the CCNA with Etherchannels, NTP, and Port-Security.
Since this lab focuses on implementation, it comes with a lab. Using the link below, you can download for free a Packet Tracer lab.
Download the lab and unzip it, then simply run it with Packet Tracer. Your goal is to complete the lab, respecting the requirements below. If you struggle doing so, don’t worry, we also have the solution (just scroll down).
Skill Integration Challenge: Etherchannels, NTP, Port-Security
This lab is a skill integration challenge. Like any challenge, you will need to put some effort into it: try to solve the lab on your own. You can do it by reading the requirements. However, you will need to understand the technologies of this lab (etherchannels, NTP, and Port-Security). In case you don’t, we won’t add any explanation here. Instead, just use these resources:
- Configure and Troubleshoot Cisco PortChannels
- NTP Configuration on Cisco Devices
- Configure and Troubleshoot Port Security
Lab Topology
The topology for this lab is fairly simple. As you can see in the picture, we can only count six devices in total.
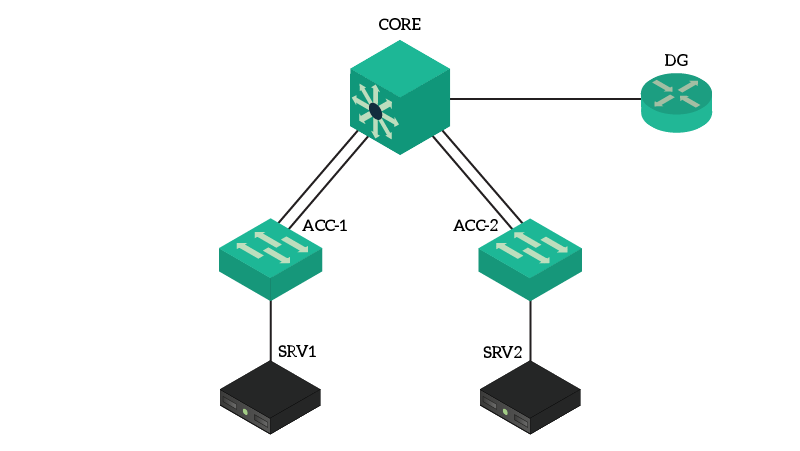
We have a router, which acts as the default gateway (and it is named DG indeed). Then, we have a dummy core switch, which merely acts as a Layer 2 device, and two access switches connecting two servers. SRV1 is the device acting as the NTP server.
The Requirements
For this lab, our ultimate scope is the basics configuration of the network. To do that, we will need to clean the STP topology with two etherchannels, add NTP on the core and the Router, and configure port-security with the NTP server. Follow these guidelines to do that.
- Configure the Etherchannels so that they use a standard (non-proprietary) protocol, and so that the Core switch is always in control of the channel. Use always 1 as the ID of the port-channel on access switches. Instead, on the core switch, use the number of the access switch the etherchannel connects to identify the channel itself.
- Add an IP address to all switches in the default VLAN so that they can communicate with each other. Prepare them for communication on different subnets as well. Follow the table below.
- On Core and DG, point to SRV1 (
192.168.1.101) for NTP. Do not use authentication. - Secure the access port connecting SRV1 to the network. Ensure that only one Layer 2 address can be seen at a time on this port, and any violation will shut it down.
| Device | IP/Mask |
|---|---|
| CORE | 192.168.1.5/24 |
| ACC-1 | 192.168.1.10/24 |
| ACC-2 | 192.168.1.11/24 |
Now, good luck! Try to implement all of that on your own. If you don’t reach a 100% score, then just read the solution below and learn from your errors.
Integrating Etherchannels, NTP and Port-Security
#1 – Configure Etherchannels
To begin this lab, we need to configure Etherchannels (or PortChannels). The requirements tell us that we need to use a standard protocol, which of course is LACP (PAgP is Cisco proprietary). We also know that the Core switch must control the aggregation, which means it must be active, while the other switches must be passive. Furthermore, we need to respect the naming of the channels. On the Core switch, we need to use the number of the connected switch. This means that PortChannel 1 will connect ACC-1, and PortChannel 2 will connect ACC-2. Instead, on the access side, we always use 1 as ID. To implement all of that, we can start by adding these commands on ACC-1.
interface FastEthernet0/10
channel-group 1 mode passive
interface FastEthernet0/20
channel-group 1 mode passiveThese commands on ACC-2…
interface FastEthernet0/11
channel-group 1 mode passive
interface FastEthernet0/21
channel-group 1 mode passiveAnd, finally, these on CORE.
interface FastEthernet0/10
channel-group 1 mode active
interface FastEthernet0/20
channel-group 1 mode active
interface FastEthernet0/11
channel-group 2 mode active
interface FastEthernet0/21
channel-group 2 mode activeHow did we get the Interface numbers? That’s fairly easy, with show cdp neighbors. In fact, this tells us which are the devices directly connected to our switches.
#2 – Basic Connectivity
The next step is to give basic connectivity to the three switches. We will need to configure an IP address on each of them in the default VLAN (which is VLAN 1). Following the table given in the requirements, we need to add these commands on ACC-1.
interface Vlan 1
ip address 192.168.1.10 255.255.255.0
no shutdown
ip default-gateway 192.168.1.1These on ACC-2…
interface Vlan 1
ip address 192.168.1.11 255.255.255.0
no shutdown
ip default-gateway 192.168.1.1And these on CORE.
interface Vlan 1
ip address 192.168.1.5 255.255.255.0
no shutdown
ip default-gateway 192.168.1.1Note that adding no shutdown is very important. The VLAN interface is shut down by default, and this means that the switch won’t use it to communicate. Furthermore, ip default-gateway is mandatory to communicate with remote subnets. However, in real-life, it won’t work on a Layer 3 device like the Core switch. If a device understands routing, as this switch does, it won’t care about that command, but instead, check for static routes.
To change that, we need to turn off the routing feature with the following command.
no ip routing#3 – NTP Configuration
Configuring NTP is fairly easy, as the server is already in place. We simply need to connect to the Core switch and to the Default Gateway and give this configuration command.
ntp server 192.168.1.101We could do that on the other devices as well, but the requirements don’t tell us to do so.
#4 – Port Security Configuration
Finally, we need to implement Port Security. This feature enables very basic access security: it is simple to enable and it protects you from some common attacks. As by requirements, we need to allow a single MAC address on the port connecting the server. Furthermore, if we see more than one (a violation happens), we want to shut down the port. These are the default actions, so we don’t need to specify them.
As a result, we will simply force the port in access mode and then enable port-security. On ACC-1, type:
interface FastEthernet0/1
switchport mode access
switchport port-securitySome thoughts
Congratulations! If you had the chance to review your lab with the solution, you should have a score of 100%. You now know how to create a basic campus network, and how to integrate etherchannels, NTP, and Port Security, three common features of any network.
Just note that, in real life, you don’t enable port-security toward servers. Servers are in a protected environment, and you generally trust them. Therefore, there’s no need to use port-security. On top of that, servers heavily rely on hardware virtualization, and each physical server is in reality a “box” containing many virtual servers. Those virtual servers are connected together with a software switch running on the physical server, which then connects to your switch. From a network perspective, a server looks a lot like another switch (hosts many MAC addresses, connects with Etherchannels & Trunks, etc.).
So, what are your thoughts about this lab? Do you feel confident in working on a campus network? What are the trickiest parts you encountered while solving this lab? Just let me know in the comments.