A true network engineer has several tools in his belt. Above all, the first tool you are going to use is ping. We are talking about a dramatically simple shell command that allows you to perform connectivity tests. Ping leverages ICMP packets to check if you can reach a host, and verify that this host is alive. Even if this technology is simple, in this article we are going to disclose all the details you need to know. After reading this article, you will know exactly how ping works. It is time to start!
ICMP Packet
When you issue a ping, you send an ICMP Request message to a target host. Based on the response you might eventually get, you know if that host is reachable.
ICMP is a stateless protocol directly encapsulated into IP, not using neither TCP nor UDP. Since its stateless nature, it can be compared to UDP in the way it works: no session establishment, no acknowledgments. Unlike transport layers protocol that uses application ports, ICMP does not use a port. Therefore, ICMP is a protocol working at the network layer, since it does not identify applications. Below, its header.
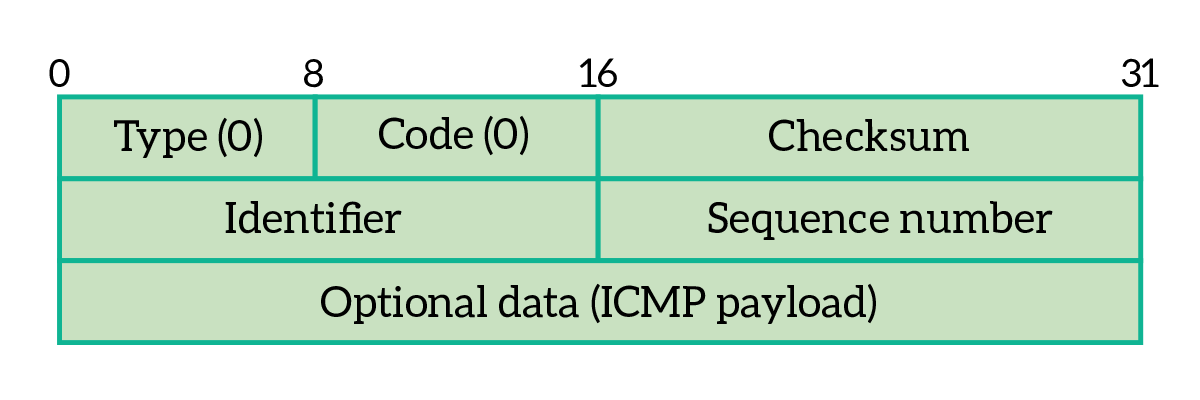
As from the picture, the header of ICMP packet is extremely simple. You can squeeze it into a 32 bits PDU! Moreover, this protocol doesn’t transport any data, making it very lightweight. Below, the description of the fields in the header.
- Type – indicates the type of ICMP packet, or – in other words – its purpose
- Code – adds details about the purpose of the packet, you can think of it like “sub-type”
- Checksum – header checksum
- Identifier, sequence number and rest of header – this varies depending on type and code fields
It would be confusing to present all different types and codes of ICMP packets right there. Instead, we will present them as we disclose the usage of ping and ICMP.
Ping: how to use ICMP
Ping for connectivity tests
The simplest thing you can do with ICMP is a connectivity test. You ping a destination IP address and see if it replies back. Just that simple. To do that, open your command prompt and type ping followed by the destination IP address. If DNS is working, you can also ping an FQDN (e.g. ping ictshore.com).
When doing so, you are using Type 8 and Code 0, which means Echo Request. If the host on the other end replies as we expect, we will see an interesting value, the TTL.
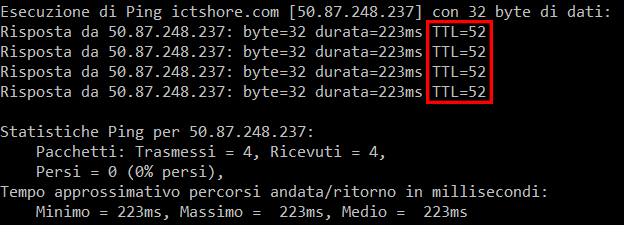
From that output, we know that ictshore.com is reachable at the IP address of 50.87.248.237. Moreover, we can see the Time-to-live (TTL) too. This field is set in the IP packet when the target device replies. Then, each router in the path decreases this value. Unix/Linux systems start always with 64, while Windows-based systems starts always with 128. Since it is extremely unlikely to have more than 20 routers between two devices, we know that ictshore.com is a Linux-based device. Here’s what it looks like.
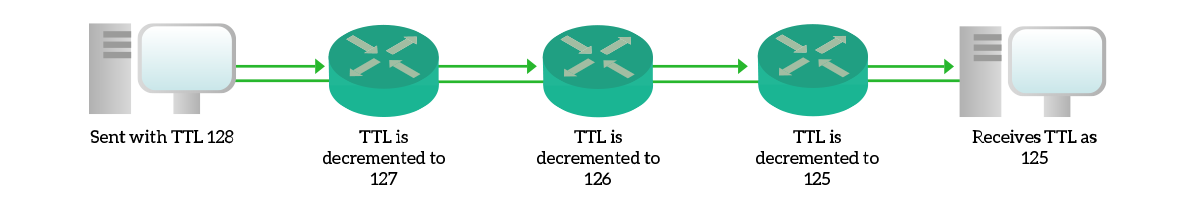
The main purpose of TTL is to prevent loops. In fact, if a router receives a packet with a TTL of 0, it simply drops the packet. This way, any packet left looping in the network (bouncing from a router to another) will be suppressed after some time.
In case the target device is not responding, we won’t see any reply. Instead, we will see a “Request timeout” message.
Tuning ping on Microsoft Windows
Some people just ping, other people ping like experts. With this powerful tool, you can do a little bit more than testing connectivity. You can verify the stability of the line, gather statistics and retrieve FQDNs. Here’s the syntax you can use.
ping [-a] [-l size] [-t | -n count] destination-ipThe text between square brackets is optional (they are options indeed). Microsoft offers you several options, but these four options are the ones you want to use.
-aretrieves the FQDN of a device from the IP (this works only if a PTR DNS record is set, but why don’t give it a try?)-l sizeset the size in bytes of the entire ICMP packet, filling it with useless content (padding). You can use this option to stress the link and see if it can handle your traffic. The default is 32 bytes.-trepeat ping until you stop it by pressingCtrl+C.-n countrepeat ping “count” times. Default is 4 times, cannot be used together with-t.
Interesting ICMP messages
ICMP is much more than a simple tool for connectivity tests. Some devices may generate ICMP packets under certain circumstances. Generally speaking, ICMP is sourced in the network when something is not going as it should. However, note that many network administrators disable this behavior because it can lead to security weaknesses. The table below presents the most interesting combination of Type and code and the related meeting.
| Type | Code | Description |
|---|---|---|
| 0 | 0 | Echo reply |
| 1-2 | All | Reserved |
| 3 | 0 | Destination network (subnet) unreachable |
| 3 | 1 | Destination host unreachable |
| 3 | 2 | Destination protocol unreachable |
| 3 | 3 | Destination port unreachable (leveraged by traceroute) |
| 3 | 4 | The path requires fragmentation, but the packet contains DF flag |
| 3 | 13 | Communication administratively prohibited |
| 5 | 0 | Redirect datagram for network |
| 5 | 1 | Redirect datagram for host |
And that’s all! Now you know what ping and ICMP are, and – most importantly – you know how to use them!
