If you are a little bit geek like me, chances are you have heard “Proxy Server” at least once. Even if you have heard about Internet Proxy, or simply “Proxy”, we are still talking about the same thing. In this article, we will demystify this scary networking device. To do that, we will explain what is a proxy server, what are its uses, and why you should know that.
A brief introduction to HTTP
Before answering “what is a proxy server”, we need to talk about HTTP. HTTP stands for Hyper-Text Transfer Protocol, and it is the language your PC uses to talk with web servers. Whenever you navigate to a website, your PC uses this protocol to ask the server the page you want. Always using HTTP, the webserver will send back the web page requested. HTTP is dead simple. It works as simple as that: the client (your PC) makes a request, and the server gives a response. Done!

Since HTTP does not bring any security feature to the table, we tend to use HTTPS. This new protocol is simply HTTP Secure, and it works exactly like HTTP but encrypts the message. With it, only the sender and the receiver understand the content, the devices in the middle don’t. Besides that, everything is the same.
What is a Proxy Server?
To put it simply, a Proxy Server is a network device that makes HTTP and HTTPS requests on your behalf. Without a proxy, you contact directly the web server and ask “Hey, give me this page”. Instead, by using a proxy you never talk with the web server, but just with the proxy. Thus, you will say something like “Hey Mr. Proxy, go to that web server and get this page for me”.
A Proxy Server is a network device that makes HTTP and HTTPS requests on your behalf.
When you have a proxy, you initiate an HTTP or HTTP request to the proxy. Then, the proxy initiates a separate request to the desired web server. While doing so, it keeps your request waiting. As soon as the proxy receives a response from the remote web server, it relays that response to you.
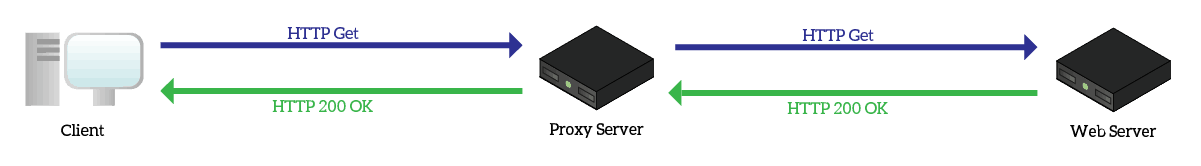
You can clearly see that this adds complexity to the process, and make it even a little bit slower. What is the point of using a proxy, then? There are several reasons you may want to use a proxy, just continue reading. Tip: Proxy Servers can support other TCP-based protocols, like FTP.
Why use a Proxy Server?
Depending on what you want to do, a proxy can help you with security, privacy, and even connection speed.
Using a Proxy Server for Security
Internet Proxy Servers find their place mainly in midsize and large companies. Such companies use them for security reasons. In fact, a proxy does not simply make requests on your behalf. It can check what pages you are going to, and eventually block some of them. This way, the company can ensure employees does not navigate to malicious websites that may harm the business. But the security a proxy adds does not end with filtering what employees do. If you have a proxy in a company, you are likely to configure the network to block direct traffic to the Internet. This way, users’ devices cannot access the Internet without passing to the proxy. This does not only force employees to use the proxy, it also makes life harder for viruses. Many viruses try to reach the Internet, and they can’t if you prevent this entire flow. The infrastructure to do that will look like this one:
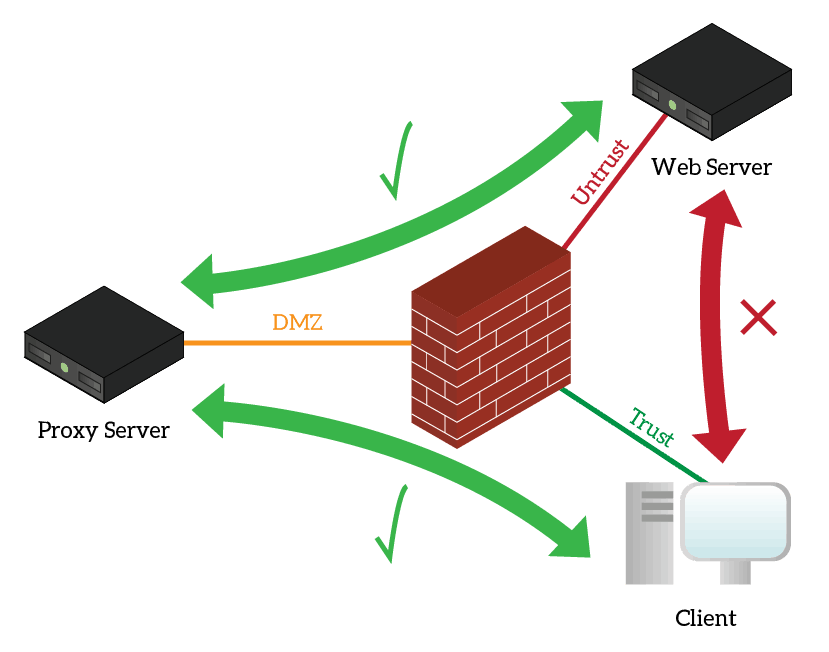
Commercial proxy is specifically designed for enterprises. Thus, they support user authentication so that you can give the different privilege of navigation to each user, and log user activities for auditing.
Using a Proxy Server for Privacy
The usage of proxy servers for privacy mainly relates to hacking and similar activities. If you navigate to a website, such a website may track information about you. In fact, it may collect your IP address and have a rough idea of where are you located. Sometimes, you may want to avoid that. Online proxies like hide.me allow you to do that. You connect to a proxy on the Internet, which makes the connection for you. This way, the target website will see the IP address of the proxy, and not yours. Of course, to do that the proxy must be on the Internet. If you deploy a proxy in your home network, it will still navigate with your IP. You can find many proxies to do that, offering several services. Some are paid, some are free, and they all claim to give you the best privacy. Of course, you will never know if they trace your connections.
Using a Proxy Server to Improve Connection Speed
We saw that a proxy re-make the request to the webserver on your behalf. This inevitably makes the process of individual requests slower, but proxies can compensate with caching. In fact, in the early days of proxies (late 90s), caching was one of the main drivers of their usage. Caching is simple. When the proxy makes a request to an external web server, it does not simply give you back the response. In fact, it also stores the response on its own memory. This way, when you make the request again, or when someone in the company does the same request, the proxy will return the response stored in its memory. While modern proxies can still enable efficiencies with caching, this function is past its best days. With modern application requirements and modern Internet speeds, caching is almost useless. Many requests are rich with user-specific data, and cannot be cached. And, even if caching as possible, it wouldn’t save much time.
How to use a Proxy Server
Now that we answered our original question “what is a proxy server”, the next question is “how to use a proxy server?”. If the proxy is up and running, all your PC needs to do is contacting it. This can happen in several ways, but before we can dive into them we need to understand SSL inspection.
HTTPS Caveats
At the beginning of this post, we stated that HTTPS enables secure communication between you and the webserver. To do that, it encrypts the data so that no middle-man can read it. This is beautiful, but what if we want to use a proxy? If the proxy simply relays any request, this is not a problem. It can forward the request “as is” without even checking its data. However, many companies want to inspect HTTPS traffic to ensure that it is not going to malicious web pages. Since the proxy is the one making the request to the remote server, it can read the response. However, it cannot relay it to the client anymore. HTTPS works with a certificate mechanism: each message is signed with a digital certificate, that identifies the original server. With mechanism beyond the scope of this article, only the original server is able to sign the message with its certificate. This means that the proxy can’t sign the HTTP message to send to the client with the same certificate of the server. When the client receives a response with a certificate different from the one expected, or with no certificate at all, it will warn the user with an ugly red page. This is because the browser detects someone doing man-in-the-middle (the proxy). In a corporate infrastructure, the solution is simple. You have to install on all PCs the trust of the certificate of the proxy so that all clients trust the certificate provided by the proxy no matter what.
Static Proxy Server
The simplest configuration for the proxy server is static. With this approach, you manually (or via script/domain policies) configure all the PCs to use the proxy. You tell each of them “Hey, contact the proxy at this address”. This is simple on Microsoft Windows and done through the Internet Options page since Windows 7. Just search for Internet Options in the start menu. Then, go in the Connections tab and click LAN Settings.
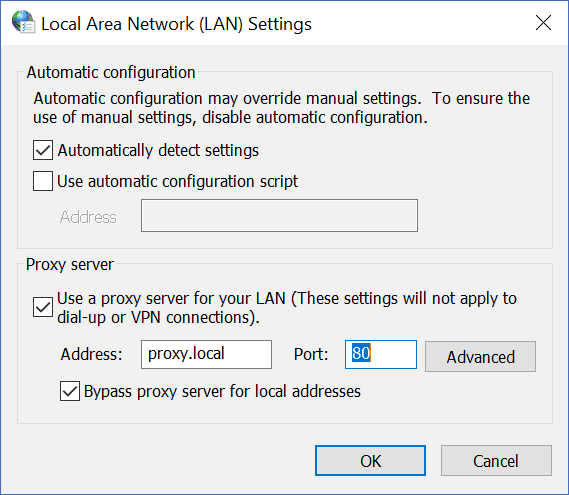
Here you can specify the details about your proxy. From there on, Internet Explorer and all other major browsers will use this proxy. However, custom applications may not rely on this “System Proxy”, but use their own settings instead. This is even more evident on Linux, where many command-line utilities have their own, individual, proxy settings. Note the Automatically detect settings and Use automatic configuration script flags: they are for WPAD and PAC, that we are just about to see.
PAC File
Using a static proxy is perfect if you have a small company where all users point to the same proxy. If you work at the Enterprise level, you may have users across different continents. For this or other reasons, you may want to have different users use different proxies, based on where the user is or which site he is trying to reach. This is where PAC comes in. PAC stands for Proxy Auto-Configuration, and it is a text file containing the rules for proxy usage. When defining this configuration, you upload this file to an internal web server and then configure clients to use the PAC. PCs will connect to the internal webserver to download the PAC file, and then use the rules inside of it to select the proxy.
WPAD
When moving from static to PAC, we shifted to a more dynamic approach. In fact, with PAC you define the rules for using the proxy centrally. WPAD goes a step even further because the client does not need to be configured to be point at anything. Instead, the client just needs to know that it should use WPAD. This is enabled by default in most operating systems, like Windows. Remember the Automatically detect settings flag in the Internet Option pages? That’s for WPAD. Once the client knows it should use WPAD, it starts the discovery process. After all, WPAD stands for Web Proxy Auto-Discovery. To put it simply, the PC ask various network devices about a proxy and will eventually get by someone “hey, use this!”. For the more technical readers, the process relies on DHCP and, as a fallback, on DNS. First, the client asks the DHCP server with a DHCPINFORM message. If it doesn’t get any response, it attempts to resolve various URL like wpad.domain.local, where domain.local is the domain of the PC. For Windows clients, NetBIOS will be used as well.
Transparent Proxy and URL Filtering
This is the most dynamic alternative. With both transparent proxy and URL filtering, the client does not need any configuration at all. In fact, the PC believes there is no proxy at all. In the case of transparent proxies, network devices like routers or firewalls redirect the traffic to the proxy. The proxy makes then the request to the external website and returns the response. This, of course, still has the HTTPS inspection issue we talked about. URL filtering is a simpler alternative to the transparent proxy, but with similar functionality. Here we have a firewall that inspects requests and responses as they pass. The key difference is that it does not makes requests on behalf of the client, it simply routes and analyzes the existing requests. This looks gorgeous. However, it has a minor flaw. Since the PC does not know anything about the proxy, it will not send authentication. This means you can’t authenticate the user and give different permissions. Some vendors implement workarounds that map users to IP addresses, but even this does not have the same precision as the client providing credentials.
Final words on “What is a Proxy Server?”
This article covers pretty much everything you need to know about what is a proxy server, and how to use it. Now you have a better understanding of the potentiality of an IT infrastructure, particularly on security. While proxies can be a pillar of security, they are generally cumbersome. They add a tremendous amount of complexity and pose challenges to the Cloud First approach. Because of that, they are gradually fading and losing importance, and they will eventually be a legacy component. Probably, URL filtering is the new trend. Yet, proxies continue to be a masterpiece of some IT infrastructure world-wide. Knowing what they are and what they do certainly add value. What do you think about Internet proxies? Do you see a bright future for them? Let me know in the comments!
