Wireshark is a powerful tool every networker needs. Until now, we have read traffic packet-by-packet, individually. While this is good, it won’t fit our needs all the time. In fact, more often than you might think, we need to see what an application is doing. In this article, we will explore some Wireshark tools that let us do it. We will explain the way to easily read the payload, and we will explain how to reconstruct a conversation. Read this carefully, as those are the Wireshark tools you are going to use every day.
Wireshark Tools and Options
Wireshark is a complex software, probably more complex than we think. It has tons of options, fine-tunings, and tools. Of course, we won’t be able to check them all in this crash course. Instead, we will see the most important ones. To show you some cool stuff, we prepared a capture containing HTTP traffic. To do the same, you just have to follow these steps:
- Open Wireshark and start a capture with no capture filter
- Open a browser (e.g. Firefox, Chrome) and surf to a website, in this example we connected to ictshore.com
- Stop the capture
Simple as that! In case you need more help in doing so, just check our introduction article to wireshark.
Following an HTTP stream
HTTP is the protocol we use every day to view web pages. In this article about applications, we explained how it works and how clients interact with web servers. If you recall your knowledge on HTTP, you will remember that it is a plain-text protocol. This means that all in all, devices are exchanging TXT files. Wouldn’t it be great to read that file? With Wireshark, you can.
As of now, we have only seen a bunch of packets presented to us like rows of a table. To see HTTP in the form of text, start by display-filtering for HTTP.
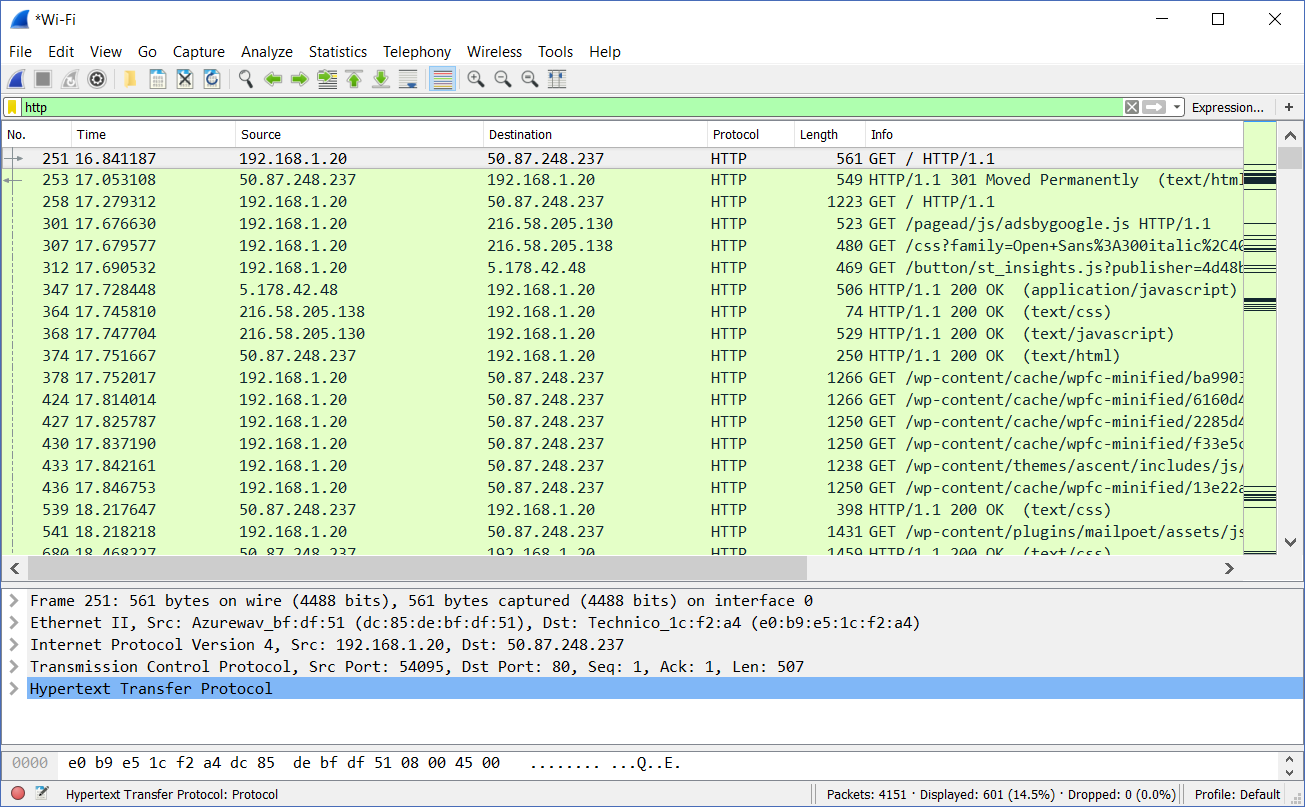
Now, from this screenshot, we can see a lot of the HTTP traffic in place. These aren’t packet, technically, they are HTTP messages. Remember, the same TCP stream hosts always two messages: a request and a response. For clarity, each message is displayed in a row. Now, we are going to use one of our great Wireshark tools to check HTTP content.
Reading the HTTP payload “as text”
To read the HTTP payload, just right-click on any of the HTTP packets. Then, find the option Follow. From there, you will have two options:
- TCP stream to read all the TCP payload of this conversation. You will see it in the form of characters not meaningful to you.
- HTTP stream is the option we are looking for, it will show both HTTP header and payload in form of plain text
Here’s the result of selecting Follow HTTP stream.
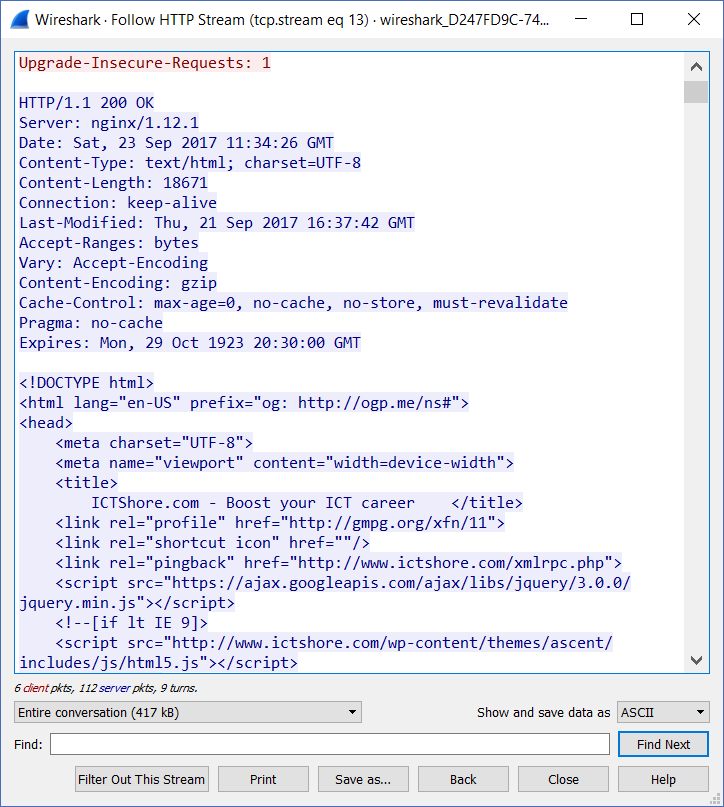
And here it is! Furthermore, Wireshark allows us to select what we want to see. At the bottom-left of the window, we can select if we want to see the entire conversation, or instead only a part of it. We can see only what the client said, or only what the server said. Furthermore, we can easily look for a specific text by using the Find text box.
This tool is one of the most useful Wireshark tools. In fact, you can use it to check application-level errors of HTTP and look for its messages.
Following other protocols
What about HTTPs?
HTTPs is the secure version of HTTP, and it is encrypted. This means that Wireshark can’t just open and read the packets, but packets will be captured and shown as HTTPs. The payload won’t be visible unless we own the private key of the server. That private key is a file that only the server’s owner has: if we have it, we can import it into Wireshark. Then, we will read the HTTPs the exact same way as HTTP.
Decrypting HTTPS, however, is for another article.
Can we follow other protocols?
Of course, we can follow other protocols, both TCP- and UDP-based. For example, we can follow Telnet and SIP. For both, the process is always the same. Start right-clicking on the packet, and select Follow. Only the available follow options will be highlighted: if the protocol is TCP-based, you won’t be able to follow UDP for example.
Capturing from other sources
Well, capturing on your own computer is great, but it might not be the most useful thing you do. After all, you are capturing traffic that your PC is already receiving. Instead, in real-life we use Wireshark mostly to analyze traffic captured elsewhere.
Port Mirroring
Port mirroring means taking the traffic going in and out of an interface, and duplicate it to another interface. In the Cisco world, this is known as SPAN (Switch-Port Analyzer). In this setup, you will put your PC on the port where duplicates are sent to.
The first step for this configuration is preparing the switch. It’s easy, you can get away by typing two commands only. You can review these concepts in this article about SPAN. Then, on Wireshark, just start a normal capture. You will see the magic of sniffing traffic.
Traffic from other devices
Many devices, like servers, routers, or firewalls, can capture traffic. Wireshark is now a popular tool, so all other devices will allow you to save captures in the pcap (Wireshark Packet Capture) format. Then, you can download those files and analyze them on your laptop. This is very useful for CLI-based devices, where it would be harder to analyze packets.
Conclusion
In this brief article, we presented some of the most powerful Wireshark tools and the best way to use them. Now, you can consider yourself proficient in Wireshark. You can use it, filter for specific traffic, and look into application data.
To foster your confidence and knowledge about this protocol, try what we presented in this article. You will soon be able to identify complex network problems by looking at the packets.
So, what are your thoughts? Has sniffing traffic ever saved your day? Just let me know in the comments.
