Any network infrastructure reflects some business needs. Nowadays, however, simply bringing connectivity to end-devices is not enough. Modern companies need connectivity to their crucial services from anywhere in the world. But it doesn’t stop just here. People want the same Internet connection they have at their desk in a meeting room. This is the need for mobility, accessing services from anywhere. However, this exposes the company to several security threats, that you need to handle with the proper infrastructure. In this article, we are going to see what solutions are out there to satisfy modern businesses.
For this article, the main goal is to give you an overview of what technologies are out there. We won’t explain any configuration command. Instead, we will give you a great high-level overview of the possibilities you have.
The driving business needs
To move technology adoptions, we always have an underlying business needs. Before starting to implement a solution, we need to understand the business needs behind it. Only with this in mind we can choose and use the best solution in any context. Nowadays, businesses can have tons of different needs, but two of them are pretty common. We are talking about Mobility and Security.

These two words may sound simple, and indeed they are. However, there’s a lot behind them:
- Mobility is the possibility for a user to move while still accessing the corporate services. This includes moving within the company’s campus, but also accessing the same services from home.
- Security is the protection of confidential information so that they are inaccessible to unauthorized users.
The fact is, mobility is a real challenge from a security perspective. This is because it virtually exposes the company to attacks from anywhere in the world, whereas without it an attacker would require to be inside the company’s walls. For now, we don’t need to focus on the conflicts between mobility and security. Instead, we should discover what are all the possibilities of both features.
Introducing Mobility
We now know what mobility is, at a high level. It’s time to dive deeper into it! We can divide mobility into two macro-categories: mobility within the company and mobility outside the company. We will analyze both.
Mobility within the Company (Wi-Fi)
Even if we didn’t write “Wi-Fi” in the title, you could have guessed it. Mobility inside a campus is all about Wi-Fi. You arrive at work with your laptop (Bring your own device politics), and you simply connect to the Wi-Fi. You don’t need a cable anymore. This is not a big deal as long as you remain in your cubicle. However, you start to appreciate it the moment you need to go to a meeting room or reach out with a colleague in another department.
With mobility, you can simply take your laptop with you and remain connected to Wi-Fi. Without any service disruption. This means that if you are watching a video, or on a Skype call, you won’t be disconnected when you are moving. You can then sit at the meeting room while you already joined the Skype meeting from your desk. Mobility allows a seamless experience across the entire campus.
This is possible through the usage of Access Points. An access point is a device that propagates the data network over thin air using 2.4GHz or 5GHz frequencies (the Wi-Fi standard). You connect that Access point to a switch, and it even supports VLANs and trunking. Then, it bridges signals from air to cable and vice-versa. In a simple deployment, you are going to have some access points, independent from one another (Cisco Autonomous Mode), as in the picture below.
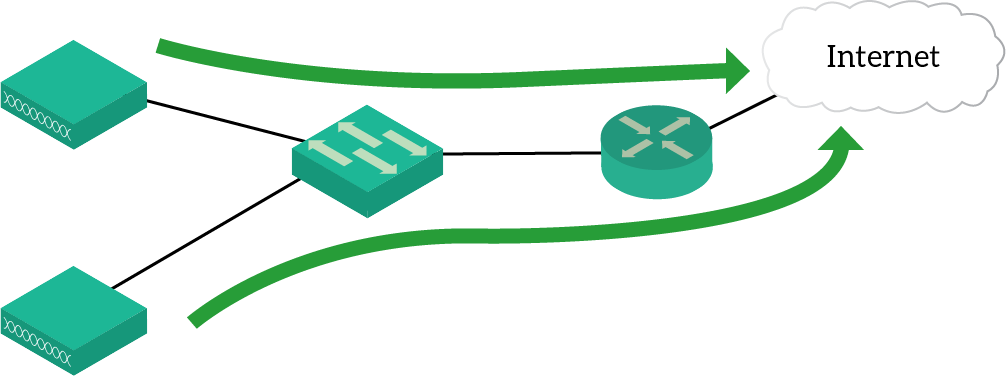
However, this might become problematic when you have many access points in a large enterprise.
Wi-Fi in large enterprises
In big deployments, you simply can’t afford to use Autonomous Mode access points. This does not give you any view on the big picture, you don’t have centralized management and you need to tune all the settings manually, potentially creating interferences between your own access points. Cisco offers you an extra device, called Wireless LAN Controller (WLC) to manage all your APs.
With a WLC, you have a centralized management plane to control your Wireless Infrastructure. You can create new networks (technically known as SSID) in minutes, and do some fine-tuning. The WLC access each access point on your behalf and configure it according to corporate policies. Moreover, it supports the dynamic replacement of APs. As soon as an AP boots, it will be looking for its WLC to get its configuration from.
With the WLC, you can configure the Access Points to send traffic to switches (like autonomous mode). However, you can also create tunnels between WLC and APs so that all the traffic from some APs passes through the WLC, like in the picture below.
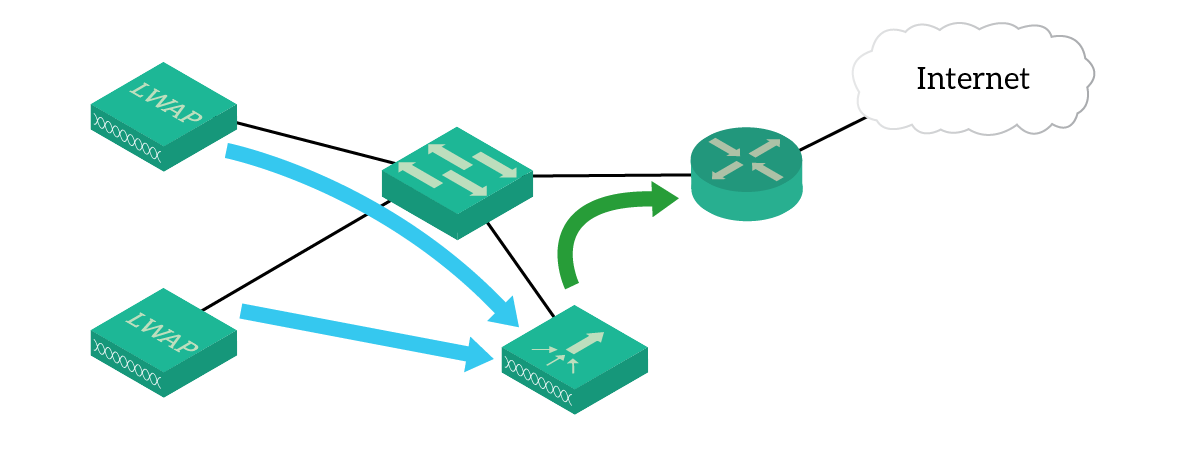
Possibilities are simply endless, and you can fine-tune your infrastructure according to needs. However, even if you move through the campus, this is not real mobility. The very big deal happens when you can access services from anywhere in the world. But before we can talk about it, we need to introduce security.
Introducing Security
Security is a mandatory requirement. There is no other way to say it. If you don’t protect your data well enough, you will be breached. It’s not about “if”, it’s about “when”. Depending on the business you are operating in, and how critical your information is, you might need different levels of security. For example, financial institutions are highly exposed and likely to be attacked. Also, Research & Development centers and patent-based businesses will require some more attention.
However, for this article, we will limit ourselves to the simplest security appliance, which is a requirement in any company. The firewall.
What is a firewall?
A firewall is a security appliance that permits or blocks traffic based on transport layer and session layer information. You can see it as a router with enhanced features. It will still support routing protocols, static routes, and traffic forwarding. However, it has a dedicated inspection engine to check every packet it receives.
On every firewall, you will find a table containing policies. Each policy defines source and destination IP address(es) and Layer 4 ports, and as an action. Every packet that has the source and destination addresses of the policy, using the ports specified, will match that policy. So, the firewall will decide what do to with that packet, based on the action. Remaining at a very simple level, the action can be either forward the traffic or drop it.
Okay, but we can do the exact same thing on Cisco routers. Kinda. With firewalls, we can have a better track of dynamic information and automatically create policies that allow return traffic. Instead, we need to do it manually on Cisco routers.
Border Security
From a network perspective, the border of an enterprise is where your network encounters other companies’ networks. A very likely example is where you encounter your provider’s network to reach the Internet. Even in small environments, you need to secure these points because you don’t trust what’s on the other side. With this approach, you are implementing security at the perimeter of your company. You are going to do this with a firewall.
Furthermore, if you have some servers that must be accessible from the Internet (like the company’s website), the firewall can play some tricks with you. With a firewall, you can segment traffic in different zones (similar to Inter-VLAN Routing) and then apply policies. With this ability, we can put all of our servers into a dedicated zone called DMZ. This stands for De-militarized Zone, an area of your network with more exposition to the Internet. This way, you won’t risk to expose your clients and workstations.
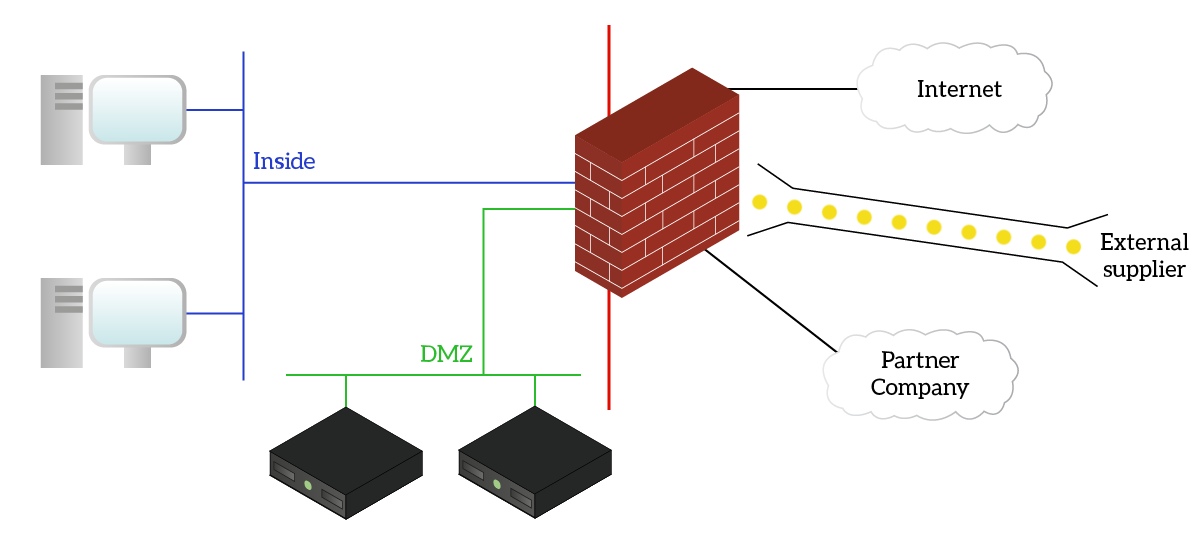
But there’s more. If you put a firewall at the perimeter, you can enable cloud adoption and remote connectivity. You can do it by using VPNs (Virtual Private Networks).
Mobility Everywhere
If you move within the same campus, you are still inside the company. Even if you move between different sites of your company, you are still in its network. The real magic starts to happen the moment you can access your company services from home. This is possible thanks to the evolution of technology, which has changed several times over the years.
A VPN, in a security context, is a secure virtual link between two points. More specifically, we mean a tunnel that connects two sites over the Internet. Traffic effectively traverse the Internet, but devices at both sites believe to be directly connected because they use a tunnel, which is direct. In reality, something is encrypting (so it’s secure) the traffic and encapsulating it into IP packets that flow into the Internet. This job is for the firewall, generally at the border of your network.
The first step in this technology was to implement site-to-site VPNs. With these tunnels, two firewalls at different sites talk with each other, and devices at both sites can use the VPN link as a direct connection. This is a very common technology we still use to connect remote sites and small branches to our headquarter or data center.
Then, the next revolution was client VPN. With this approach, you don’t need two firewalls anymore. Instead, you just keep a firewall in the headquarter. On the other side, the VPN is terminated by the client PC. Companies install on their employees laptops a specific software that can dynamically create a VPN to the headquarter. Now, whenever you have an Internet connection, you can access your company’s services.
Today, we are headed even further. With cloud adoption, company services are accessible over the web. To access them, you just need a browser and your credentials. You basically go to a website, log in and you are set to go. No VPN anymore. This way, you don’t have the requirement to use your company’s PC.
The Hidden Threats
Mobility creates security weaknesses. On the other hand, security prevents mobility. If you think about it for a moment, it will start to sound pretty obvious. Originally, all your key services were private. That is, only accessible if you were physically inside your company’s wall. With the increasing demand for mobility, we started to expose them to virtually anyone.
Now, anyone can at least try to breach your confidential information. There is a door to enter your company over the Internet. Of course, it is closed, and you need to have the key, but it’s out there. Anyone can try to open it, even forcing it. However, we can’t simply avoid mobility. This is something modern businesses want. Instead, we should try to focus on how to increase security while still enabling mobility.
Services in the cloud are pretty secure and trustworthy if correctly implemented. However, you need to go beyond a simple firewall. The world of security has evolved over time, and now we have Intrusion Prevention Systems, Next-Generation Firewalls, and more. The most interesting branch is cyber-security, which evaluates attacks that can exploit your company’s applications.
Conclusion
In this article, we have disclosed two of the most demanded enterprise services: mobility and security. With this knowledge, you are now ready to look at networks at a wider angle, considering the whole picture.
Now that we know how to structure an Enterprise network, at a very high level, we can start to go deeper into technical topics. Following the Free CCNA Course, you will see how to troubleshoot a client, configure DHCP and static security. Remaining on this path, you’ll be ready for your first certification soon.

