In our previous article, we learned the fundamental of NAT. Now, it is time to put them in practice. With this article, we are going to configure Network Address Translation in two ways. First, we are going to implement a static translation, and then a NAT Overload configuration. In this process, we will see all the commands involved in Cisco IOS, as well as some useful tips.
This article sees you configuring two routers, so it comes with a Cisco Packet Tracer lab. To benefit the most from this content, just download the lab using the link below.
Once you downloaded the lab, open it with Cisco Packet Tracer. Then, try the commands you see in the article with the lab. You will soon become a master of NAT.
NAT Configuration Lab Intro
Lab Topology
For this article, we are going to work with two sites connected over the Internet. On the left, we have a site with two clients: “Home”. This site resembles a lot a typical domestic configuration: a single router with DHCP on it, and a few clients. On the other side of the Internet, we have a tiny Data Center with a single Web Server.
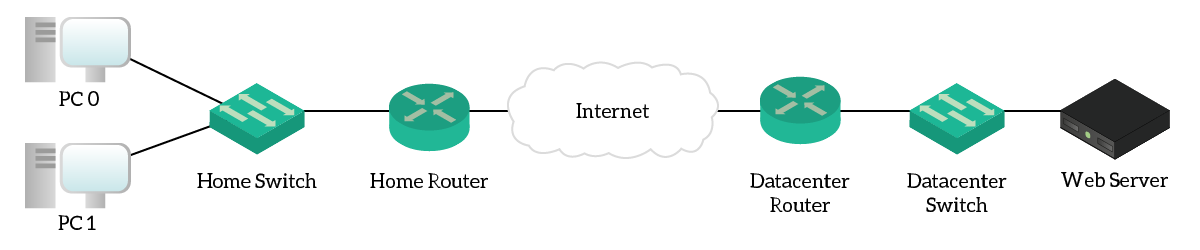
As you can see, the Internet is just a cloud. Inside of it, we put three routers to emulate a few of Internet hops. To complete this lab, you only need to configure the two Edge routers: HomeRouter and DatacenterRouter. Obviously, all the configuration we are going to do is related to NAT.
The Requirements
From a high-level perspective, we have two simple requirements: the webserver must be accessible through the Internet, and the clients must surf the Internet. As a result, trying to navigate to the Web Server address from a client is a valid test for the success of the lab. Moreover, we didn’t implement DNS purposefully: this way you will see the IP addresses. Here we have a more technical view of the two requirements:
- The web server has an IP address of
10.0.2.15/24, and we need to expose it to the Internet with the public IP of the router (16.11.38.26) - All the clients in the “Home” need to surf the Internet using the public IP of the router (
87.38.11.12)
As you will see, this will translate in just a few commands.
Configuring NAT
Before we start with the configuration, we might want to verify that without NAT nothing works. Doing that is simple, we just need to connect to a PC and do a trace to 16.11.38.26. This is the public IP of the router on the other side of the Internet, the one we want for the webserver. Here’s an example of the traceroute.
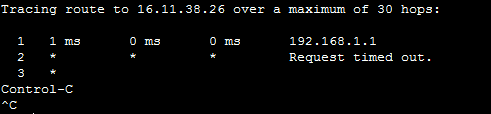
The root cause for that is no hop over the Internet knows a route back to 192.168.1.0/24 network. So, even if traffic can get through, the responses won’t make it. If we implement NAT, everything will start to work.
Static NAT Configuration
Before we can start with any fancy configuration, we need to define interfaces from a NAT perspective. The router will translate addresses from the Inside network into addresses on the Outside network. However, to do that, the router needs to know which network is inside and which is outside. We have no limitations here: you can have as many inside and outside networks, but the same network can be either inside or outside – not both.
To define that, we need to enter the interface configuration. From there, we can enter ip nat inside for the interfaces in inside networks. As you might guess, we need to use ip nat outside for the interfaces on outside networks. Here’s the configuration we need to enter.
interface GigabitEthernet 0/1
ip nat inside
interface GigabitEthernet 0/2
ip nat outsideWith these only two commands, your score will reach 28%. They are extremely important because if you don’t categorize interface correctly the entire NAT won’t work as expected.
Now, we need to create a static entry in the NAT table to tell the router “replace this IP with this other IP”. We do it from the global configuration, using the ip nat inside source static command. These commands expect to know the local IP address (the “inside source”), and the global IP address for the replacement. So, here’s what we need to type.
ip nat inside source static 10.0.2.15 16.11.38.26Configuration on the server-side is complete!
NAT Overload Configuration
As we are going to see, the configuration of NAT Overload is a little bit more tricky. To refresh your memory, NAT Overload allows us to have multiple inside IP addresses and a single public IP address. This is possible by using TCP and UDP ports for multiplexing. However, in practice, we need to define which inside addresses can be multiplexed.
Before we start, the first thing we want to do is the definition of inside and outside interfaces. Like on the other side, the HomeRouter is going to have GigabitEthernet 0/1 as inside and GigabitEthernet 0/2 as outside.
Defining the Inside addresses
Now that we have interfaces correctly in place, we can focus on the “inside source” addresses. Instead of manually entering each address, Cisco offers us a much faster way to identify them. We can define an Access List, and tell the router to use all the addresses matching the ACL as a source.
Need a refresh on ACLs? We have a great article about understanding Access Lists and another one about configuring Access Lists.
For this lab, we need to ensure that all addresses from the inside network are subject to NAT. In other words, the entire 192.168.1.0/24 subnet. Luckily for us, we can match that with a standard access list containing a single rule. So, create the Access List 1 with the command below.
access-list 1 permit 192.168.1.0 0.0.0.255This ACL is part of the score, so if you have done everything correctly you should be at 85% by now.
Creating the NAT Rule
There’s only one thing left to do: configuring the NAT Overload rule. Basically, we need to associate the IP addresses of the ACL with a public IP address and enable overload. To do that, we still use the ip nat inside source command, but with the keyword list instead of static. This keyword expects to know an ACL number: we are telling that the list of inside addresses is inside of the ACL. After that, we need to enter the interface keyword followed by an interface name. This way, we tell the router to use the IP address of that interface as the outside one. After that, as the last keyword, we need to add the overload keyword. As you might have already guessed, this effectively turns on NAT Overload for this entry. The final result will look like this.
ip nat inside source list 1 interface GigabitEthernet0/2 overloadWith this very last command, you should have reached a 100% score. Congratulations, you have mastered NAT! But continue reading, there are some things you should know about.
If you now try to surf to 16.11.38.26 from one of the two clients, you will see the web page. The traceroute will also work as well.
Dynamic NAT with pools
In the previous article about understanding NAT, we covered the concept of dynamic NAT. Just to remind you, it is not a new type of NAT. Instead, it just means having multiple public (outside) addresses and associate them dynamically to inside ones.
To implement that, we need to first define a NAT pool. This is simply a group of public addresses we can define with the ip nat pool command. This configuration command wants a name, the start IP address, and the end IP address, followed either by netmask and the netmask or prefix-lenght and the CIDR (e.g. “/24”).
Once you created a pool, you can reference it in all other NAT commands whenever you need to type a public IP address. Instead of typing that address, insert pool and the name of the pool.
It is unlikely that you will need to configure dynamic NAT, but it might be good to know.
Troubleshooting NAT
Cisco offers a simple and powerful command to check the NAT table: show ip nat translations. With that command, you can see the content of the NAT table in the moment you type the command. Here’s an example output on the router in the Data Center.
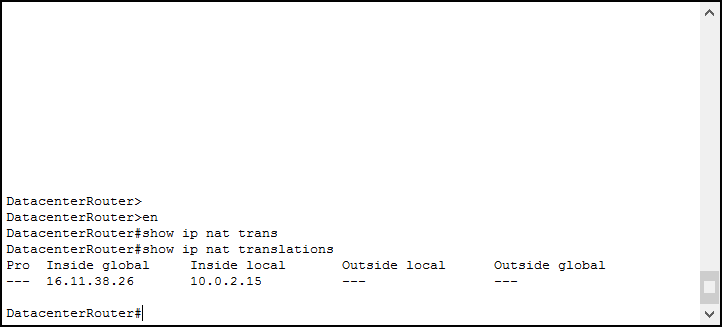
Look at the output, it shows five columns per line. We need to focus on the last four:
- Inside global is the IP address of the “inside device” as seen from the outside
- Inside local is the IP address of the “inside device” as seen from the inside, or the real IP address
- Outside local and outside global work like their “inside” counterparts, but they are used for destination NAT which is out of scope for the CCNA
Always remember that this command shows the current status in time of the NAT table. So, any dynamic rule such as NAT Overload will appear only if there is some traffic going on the moment you type the command. If you want to see if NAT is working and stable, you can issue show ip nat statistics and see if the counters increase.
Conclusion
In this article, we put into practice the concepts we learned about NAT. We created two rules, one static and another for NAT Overload. We have also seen the commands for dynamic NAT and NAT Troubleshooting. Here’s a recap of the commands you need to take with you.
- To configure static NAT, use
ip nat inside source staticfollowed by inside address and outside address - To configure NAT overload, first, define an ACL to match the source traffic, then use
ip nat inside source list - Use
ip nat poolto define a pool of public IP addresses - To troubleshoot NAT, use
show ip nat translationsandshow ip nat statistics
With the knowledge you gained with this article (and the previous ones), you are now ready to connect a small-to-midsized business to the Internet. Get ready, because with the next articles we will jump to the second part of the CCNA, facing complex and beautiful topics.